Across the Great Wall we can reach every corner in the world.
A Introduction
The regulation of data has increasingly become a common feature of trade agreements. To understand this rule framework, it is essential to first identify the main players and interests at stake. In my view, data regulation in trade agreements mainly deals with three groups of interests, each corresponding to different stakeholders. The first is the commercial interests of the companies engaged in electronic commerce. Due to the unique nature of their business, most Internet companies need unhindered data flows to conduct their business. Thus, they demand free flow of information across the globe and oppose to data localization requirements. Behind the second group of interest is the person or the consumer, who supplies the raw data to use the services provided by the Internet companies. As both the raw data and the processed data are controlled by the companies, consumers, at least to the extent they would act in their best interest, wish to ensure that their privacy and personal data are properly protected. This is where the third, and arguably the strongest, stakeholder – the state – comes into play.
The state monitors and regulates the data used by the first two groups, which involves the collection, processing, access and transfer of data. In designing the regulatory framework, the state often tries to strike a balance between the different or even conflicting interests of the different players, by trying to ensure the protection of the privacy of personal data, while not unduly hindering the development of the economy. Faced with various threats, such as cyberwarfare and terrorism, the state also needs to ensure that public safety and national security are not compromised by rogue players roaming at large in cyberspace.
While all regulators would agree on the need to strike a balance between the clashing interests of different stakeholders, their approaches often differ in practice. Some jurisdictions prioritize the need to safeguard the privacy of their citizens. A good example in this regard is the General Data Protection Regulation (GDPR) of the European Union (EU), which recognizes ‘[t]he protection of natural persons in relation to the processing of personal data’ as ‘a fundamental right’.Footnote 1 On the other hand, some jurisdictions put the commercial interests of firms first. In the United States (US), this is reflected in the 1996 Telecommunication Act, which notes that it is ‘the policy of the United States … to preserve … free market … unfettered by Federal or State regulation’.Footnote 2 In contrast, national security concerns are often cited to justify restrictions on cross-border data flow, albeit in varying degrees in different countries. A recent example is China’s 2017 Cybersecurity Law, which imposed several restrictions aiming to ‘safeguard cyber security, protect cyberspace sovereignty and national security’.Footnote 3
It is not easy to say which one is the best approach, as the various regulatory approaches often reflect the different legal, political, economic, social and cultural backgrounds of different countries. What is more important than passing judgement about different models, however, is to understand the inherent logic and mechanisms of the different regulatory regimes. In this chapter, I will focus on China, which is not only home to the largest e-commerce market in the world but also has one of the most tightly regulated cyberspaces. By providing a detailed analysis of the rationale and operation of ‘data regulation with Chinese characteristics’, the chapter seeks not only to help understand this discrete regulatory model but also to find ways to deal with such a regime at the international level.
B Internet Regulation in China
The first email from China was reportedly sent on 20 September 1987 by a group of researchers at the Institute for Computer Science of China’s State Commission of Machine Industry to the University of Karlsruhe in Germany.Footnote 4 On 28 November 1990, China’s national domain name – ‘.cn’ – was registered by Professor Qian Tianbai, a pioneer in the Chinese Internet industry.Footnote 5 However, it was not until 20 April 1994 that the first connection to the international network was established by China Education and Research Network, which marked the launch of the Internet in China.Footnote 6 Since then, the Chinese Internet has grown by leaps and bounds, despite occasional hiccups, such as Google’s exit from China in 2009.Footnote 7 In 2013, China’s e-commerce volume exceeded 10 trillion RMB and China overtook the United States as the largest e-commerce market in the world.Footnote 8 Nowadays, Chinese e-commerce giants like Alibaba are among the biggest online retailers globally and Chinese online shopping festivals, such as the Singles Day (11.11) Sale have gained loyal followers all around the world.Footnote 9 In the latest race on the research and applications of big data, machine learning and artificial intelligence (AI), China is also quickly catching up with the United States, a world leader that increasingly sees its competitive edge being narrowed.Footnote 10
Notwithstanding the phenomenal growth in the e-commerce sector, the Internet remains under tight regulation in China. The following section provides a detailed examination of this framework, paying specific attention to the regulation of data.
I Overview of the Regulatory Landscape
Just like the development of the Internet in China, the evolution of the regulatory landscape in China over the past twenty years is also a remarkable journey, where the haphazard regulatory patchwork was revamped in several iterations before culminating in one of the most sophisticated regulatory frameworks the world has ever seen. With the benefit of the hindsight, we can divide the development of the regulatory framework into four stages.
The initial stage was from 1987 to 1998, when the Internet was still in its embryonic stage and the government had yet to fully fathom its potential. Thus, the world wide web largely remained as the ‘wild wide web’ and untangled by regulations. This does not mean that there was no regulation at all during this period. To the contrary, two important regulations were introduced in the short span of one year – the 1996 Provisional Regulations on the Management of International Networking of Computer Information NetworksFootnote 11 and the 1997 Measures for Security Protection Administration of the International Networking of Computer Information Networks.Footnote 12 Yet, the regulatory framework in this period suffered from the following weaknesses: First, these regulations were very low in the legislative hierarchy, as they were provisional regulations and administrative rules issued by the executive branch, which did not have the same force as national laws issued by the National People’s Congress (NPC) and its Standing Committee. Moreover, these regulations were not made with the authorization of the legislature. Thus, at least in theory, these regulations could be challenged, especially with regards to provisions that contradicted the rules in legislations of a higher rank. Second, the regulatory framework was built in a piecemeal manner. There was no central agency coordinating the powers of the different agencies and no clear delineation of jurisdictions between the different agencies. This could potentially result in gaps as well as in overlaps in the regulatory framework, making the whole system rather inefficient. Third, these regulations all focused on the Internet hardware and there was no regulation on the software, not to mention content. Paradoxically, this contributed to the exponential growth of the Chinese cyberspace at the turn of the century, where people flocked in the pursuit of freedom of speech unavailable offline.
The second stage started with the establishment of the Ministry of Information Industry (MII) on 31 March 1998, which resulted from the merger of the Ministry of Posts and Telecommunications (MPT) and the Ministry of Electronic Industry (MEI).Footnote 13 With an explicit jurisdiction over the information industry, the MII became the main regulator of the Internet in China.Footnote 14 However, other agencies quickly stepped into the cyberspace and started to compete with MII on the regulation of various issues such as online news, audio-visual services, online media and web security.Footnote 15 While these new agencies helped to fill the void in the regulatory space, their eagerness to capture more regulatory power also heightened the risk for potential turf wars. To address this, in 2001 the State Council re-established the National Informatization Leading Group.Footnote 16 Headed by then Premier Zhu Rongji, the Leading Group tried to coordinate among the different agencies. In November 2004, the General Office of the CCP Central Committee and the General Office of the State Council issued Opinions on Further Strengthening Internet Administration, which clearly divided the jurisdiction and responsibilities of all central government ministries and agencies involved in Internet governance.Footnote 17 However, as these agencies are all of the same ministerial rank, the problem of regulatory competition remained. This did not change until 2010, when the General Office of the CCP Central Committee and the General Office of the State Council issued Opinions on Strengthening and Improving Internet Administration.Footnote 18 Pursuant to the Opinions, the Cyberspace Administration of China (CAC) was established in 2011 as a ministerial-level agency.Footnote 19 While its main jurisdiction is content regulation, the CAC also presides over the troika of Internet governance, which includes, in addition to the CAC: the Ministry of Industry and Information Technology (MIIT), which inherited the portfolio of the MII; and the Ministry of Public Security (MPS), which is responsible for Internet crimes and safety issues.Footnote 20
The third stage in the evolution of China’s cyberspace regulation was heralded in 2013 by the Third Plenum Conference of the Eighteenth Party Congress, which adopted the Decision of the CCP Central Committee on Several Major Issues concerning Comprehensively Deepening Reform.Footnote 21 The Decision adopted the policy of ‘positive adoption, scientific development, lawful administration and ensuring security’ for the development of the Internet, and called for further strengthening of Internet governance, especially the further streamlining of its leadership system. Most notably, the Decision emphasized that the objective of Internet governance shall be ensuring ‘the security of national Internet and information’. This was the first time that Internet governance was elevated to the level of national security in a major Party document, and it set the tone for a new era of China’s Internet regulation.
In his report to the Third Plenum Meeting, President Xi covered eleven major issues, one of them being Internet governance.Footnote 22 He emphasized that Internet and information security is ‘a matter of national security and social stability, and a new composite challenge facing China’.Footnote 23 Xi also noted that the existing Internet governance system was lagging behind the rapid development of Internet technology and applications, and suffered from problems such as duplication and overlapping of agencies and their jurisdictions, mismatch between power and responsibilities, and low efficiency. According to Xi, to further strengthen Chinese Internet governance, the functions of the relevant agencies needed to be reshuffled to provide a comprehensive governance framework that covered everything from technology to content, and from ensuring everyday security to combating crimes.
Pursuant to the Third Plenum Decision, the Central Leading Group on Cyber Security and Informatization was established in February 2014.Footnote 24 The Leading Group is the third ‘super agency’ established after the Third Plenum Meeting, with the other two in charge of the most important topics – comprehensively deepening reform and national security, respectively. With President Xi as its head and Premier Li Keqiang as the deputy, the Leading Group has twenty-two members, which include three of the seven members of the Politburo Standing Committee and nine of the twenty-five members of the Politburo. Eleven of its members are also members of the Leading Group on Comprehensively Deepening Reform, one is Secretary-General of the State Council at Vice Premier level, while the rest are all heads of important ministries, including the all-powerful National Development and Reform Commission. Such high-level set-up signals that cyber security and informatization have been elevated to an unprecedented level and have now become important components of the overall national security strategy.Footnote 25 While the Leading Group remains an ad hoc body, it now has an office housed at the newly restructured Cyberspace Administration of China (CAC).Footnote 26 This greatly boosted the status of the CAC among the peer ministries, as it is one of the few agencies under direct leadership of President Xi. In August 2014, the State Council even delegated its power on cyberspace content regulation to the CAC.Footnote 27 This made the CAC the most powerful agency with regard to the regulation of the Internet, and particularly with regard to Internet content.
The emphasis on cyber security was further confirmed by the 2015 National Security Law, which considers cyber security as a key component of national security and directs the state to make the ‘core technology of the Internet and information, key infrastructure and the information system and data in key areas secure and controllable’ in order to ‘protect national cyberspace security, safety and development’.Footnote 28 Moreover, Article 77 of the law requires all citizens and organizations to make timely reports on activities that endanger national security, truthfully provide evidence relating to such activities that one knows of, and provide the necessary support and assistance to national security agencies. If enforced strictly, the provision could be used to compel netizens to report ‘harmful information’ or activity in cyberspace, and throw China back to the days of the Cultural Revolution, where everyone was under the constant surveillance of each other. In practice, however, this clause has not yet been employed in such an aggressive manner by the authorities.
The evolution of China’s Internet regulation finally culminated in the 2016 Cyber Security law, which emphasized in the first article that cybersecurity is a matter of cyber-sovereignty and national security. The heightened role of the CAC was also further cemented by Article 8 of the law, which entrusted it with the overall responsibility for the planning and coordination of cybersecurity work and relevant supervision and administration, while the other ministries, such as the MII and MPS, are only responsible for the cybersecurity administration within their own jurisdictions.
II China’s Main Internet Regulations
From early on, the Chinese government recognized the disruptive potential of the Internet and put it under strict regulation. For example, barely two years after China was connected to the Internet, the State Council issued the very first Internet regulation – the 1996 Provisional Regulations of the People’s Republic of China on the Management of International Networking of Computer Information Networks (‘Provisional Regulations’).Footnote 29 According to Article 3, the Provisional Regulations apply to all international networking of computer information networks within China, which is defined as ‘networking of the computer information networks inside the People’s Republic of China and those in foreign countries with the purpose of international exchange of information’. The key provision is Article 6, which provides that ‘computer information networks shall use the international entry and exit gateways provided by the Ministry of Posts and Telecommunications in the country’s public telecommunications network when they carry out direct international networking. No units or individuals shall be allowed to establish or use other channels for international networking without authorization’.
Anyone found in violation of the provision could be punished with a fine up to 15,000 RMB,Footnote 30 which was a hefty amount in 1996. With merely seventeen articles, the Provisional Regulations seem rather rudimentary, especially considering the fact that it dealt with such a complicated subject matter as the Internet. However, upon closer examination, we can say that it actually encapsulated all three aspects of Chinese Internet regulations for the decades to come.
The first is hardware regulation, which mandates that all Internet connections must go through official gateways sanctioned by the Chinese government. Such regulation enables the Chinese government to effectively control Internet connection, especially in blocking and filtering certain international websites and services.
The second is software/applications regulation, which means that even the software for Internet access must be sanctioned by the government. This is indicated in Article 10 of the Provisional Regulations, which states that all individuals, legal persons and other organizations must connect to international networks through access networks, which in turn are required by Articles 6 and 8 to connect through the Internet, i.e., those international gateways sanctioned by the MPT. This requirement is made explicit in the Implementation Rules for the Provisional Regulations (‘Implementation Rules’) promulgated by the Leading Group for Information Technology Advancement under the State Council on 13 February 1998.Footnote 31 After repeating the requirement to use official international gateways and the prohibition on using other gateways in Article 7, the Implementation Rules went on to state in Article 10 that all access networks to international networks shall go through the Internet and international network connections through ‘any other means’ are explicitly prohibited. According to Article 3.3 of the Implementation Rules, the international entry and exit gateways are ‘physical information channels used for international networking’. As Article 7 already explicitly prohibits the use of other physical gateways for connection, the interpretation of the law means that the term ‘any other means’ shall be interpreted broadly and includes other connection methods at both the hardware and software/applications levels. In other words, the term ‘any other means’ includes not only other physical gateways, but also ways to connect to the Internet through software such as virtual private network (VPN). This stringent requirement is repeated in Article 12 of the Implementation Rules, which further affirms that all individuals, legal persons and other organizations must connect to international networks through the access networks and not ‘any other means’.
The third category of regulation regards content. Again here, the essential rule framework on content is already found in the Provisional Regulations, which states in Article 13 that ‘the organizations and individuals conducting international networking businesses shall abide by relevant State laws and administrative decrees and strictly follow safety and security rules. They shall not use international networking for law-breaking or criminal activities that may endanger national security or divulge State secrets; or producing, consulting, duplicating or propagating information that may disturb social order or pornographic information’.
This strict regulation is also duly copied into Article 20 of Implementation Rules, with two small but significant twists. First, the subject of regulation expands from those conducting international networking businesses to the access units (Internet service providers, ISPs) and users. This makes sense, as the bulk of the content online is usually created by intermediaries and end users. Second, the same article also requires the three groups to immediately report any harmful information they discover to the relevant authorities and take effective measures to prevent the dissemination of such information. This is yet another important feature of Chinese Internet regulation that differs from other countries, especially the United States, which do not impose liabilities on ISPs pursuant to the ‘safe harbour’ rule. As we will see later, this approach has been extended to the regulation of data in recent years.
In the sections that follow, we examine the main Chinese Internet regulations along the three themes of hardware regulation, software regulation, and content/data regulation.
1 Hardware Regulation
According to Article 8 of the Implementation Rules, the nascent Internet in China is broken down into four networks: China Public Computer Network (CHINANET), China Golden Bridge Network (CHINAGBNET), China Education and Research Network (CERNET) and China Science and Technology Network (CSTNET), which are respectively administered by the MPT, the MEI, the State Education Commission, and Chinese Academy of Sciences. Among the four, the first two are commercial networks, while the last two are non-profit networks, which provide Internet services for the universities and research institutes under their respective jurisdictions. In 2000, China Mobile, the largest mobile company in China, also received approval to build an international Internet gateway.Footnote 32 To further regulate international gateways, the MPT issued Administrative Rules on International Networking Entry and Exit Gateways for Computer Information Networks,Footnote 33 which reiterated the prohibition on international networking through self-established international networking or other means including satellite.Footnote 34 The 2000 Telecommunication RegulationFootnote 35 also stated that all international telecommunication services shall go through the approved international gateways,Footnote 36 and explicitly prohibited operating international networking business through leasing dedicated international telecommunications lines, establishing relaying facilities without permission or other means.Footnote 37 To avoid confusion as to whether Internet services were part of telecommunication services, the Telecom Regulation also explicitly stated that both Internet connection service and Internet information service are part of value-added telecom services.Footnote 38
When China acceded to the World Trade Organization (WTO) in 2001, the hardware restriction was also copied into its Schedule of Specific Commitments for Services, which notes that ‘[a]ll international telecommunications services shall go through gateways established with the approval of China’s telecommunications authorities’.Footnote 39 There was considerable confusion as to whether China’s commitments include Internet services. On the one hand, its commitments on value-added telecom services seem to include all the value-added telecom sub-sectors under the Services Sectoral Classification List – that is, h. Electronic mail; i. Voice mail; j. On-line information and database retrieval; k. Electronic data interchange; l. Enhanced/Value-added facsimile services (including store and forward, store and retrieve); m. Code and protocol conversion; n. Online information and/or data processing (including transaction processing). The only restriction seems to be that the services shall be provided through a joint venture with 50 per cent cap on foreign equity. On the other hand, China’s Telecom Regulations list Internet connection services and Internet information services separately from the value-added telecom services listed earlier. One may argue that one of the value-added services listed in China’s schedule – online information and/or data processing (including transaction processing) – has the CPC number 843**, which corresponds to online content services in the current CPC version.Footnote 40 However, a closer examination reveals that the correspondence is only superficial, as the two Internet services under the current CPC version correspond to 75231 and 75232 in the CPC provisional list (‘CPCprov’),Footnote 41 which is the basis of Services Sectoral Classification List and thus for the GATS negotiations and commitments. Class 7523 is defined in CPCprov as ‘data and message transmission services’, which in turn can be broken into Subclass: 75231 – data network services, and Subclass: 75232 – electronic message and information services.Footnote 42 However, according to the explanatory notes, Class 7523 only covers the necessary network services (mostly the underlying hardware) for data transmission, rather than the provision of information online. Thus, at most, China’s schedule would only cover Internet connection services but not Internet information services. However, even such an interpretation cannot get around the requirement to go through officially sanctioned international gateways, which is repeated ad nauseam in the regulations mentioned above and China’s GATS schedule.
2 Software Regulation
As mentioned earlier, the Implementation Rules prohibits connection to international networks through ‘any other means’, which could include software designed to evade official international gateways in addition to hardware. This is also copied into Article 59.1 of the Telecom Regulations, which prohibits the operation of international networking businesses through any means. The 1997 Measures for Security Protection Administration of the International Networking of Computer Information Networks provides further clarification by prohibiting unauthorized access to or use of computer information networks, which could cover access to international network using unauthorized software.Footnote 43
After Google pulled out of China in 2009, the Chinese government continued to tighten its control on cyberspace and blocked the websites of major social media (Facebook, YouTube, Twitter, etc.) and major international media (Bloomberg, Reuters, New York Times, etc.). To access these websites, many netizens resorted to VPNs. In view of this, the MIIT issued a notice in 2017, which explicitly prohibited VPNs.Footnote 44 To minimize the impact on firms, MIIT later clarified that foreign trade firms and multinational corporations could still lease dedicated lines for international networking from authorized telecom operators.Footnote 45 However, according to MIIT, such private networks can only be used for the internal office needs of the firm, and cannot be used to connect data centres or platforms abroad to conduct telecom businesses, which means that the lines cannot be leased to private consumers who are not employees of such firms. Since then, China has launched a major campaign to crack down on VPNs, and people have been jailedFootnote 46 and fined for selling and using VPN services respectively.Footnote 47
3 Content/Data Regulation
The main content regulation is the 2000 Administrative Measures on Internet Information Services,Footnote 48 which states in Article 15 that Internet Information Service Provider shall not produce, copy, distribute or disseminate information that is contrary to the basic principles laid down in the Constitution, laws or administration regulations; is seditious to the ruling regime of the state or the system of socialism; subverts state power or sabotages the unity of the state; incites ethnic hostility or racial discrimination, or disrupts racial unity; spreads rumours or disrupts social order; propagates feudal superstitions; disseminates obscenity, pornography or gambling; incites violence, murder or terror; instigates others to commit offences; publicly insults or defames others; harms the reputation or interests of the State; or has content prohibited by laws or administrative regulations.Footnote 49
Apparently copied from the Telecom RegulationsFootnote 50 and 1996 Interim Regulations on Electronic Publications,Footnote 51 the list has remained largely constant for the past twenty years. The only addition was made in 2002, when several regulations added a new category of ‘harming the social morality or the excellent cultural traditions of the nationalities’.Footnote 52 This new category, however, seems to be restricted mainly to online publications and has not been incorporated into subsequent laws and regulations. For example, neither the Administrative Measures on Internet Information Services nor the Telecom Regulations added this new category in their 2011 and 2016 amendments. It is also worth noting that such stringent regulation is not restricted to the Internet sector, as other regulations in the same period share the same restrictions on content.Footnote 53
One apparent gap in the 2000 Administrative Measures is that the rules apply only to Internet information service providers but not the users who generate such information. This gap was filled by the 1997 Measures for Security Protection Administration of the International Networking of Computer Information Networks, which expands the liability to ‘any organization or individual’.Footnote 54 In judicial practice, the offense of ‘Picking Quarrels and Provoking Trouble’ has also been invoked on a case-by-case basis against people posting information online about various social problems. One example is the case of Zhao Lianhai, who was jailed for two-and-half years for trying to collect information about contaminated milk with a self-built website.Footnote 55 In 2013, the practice was further institutionalized when the Supreme People’s Court and Supreme People’s Procuratorate jointly issued a judicial interpretation, which clarifies that posting defamatory information online would be subject to the offence of criminal defamation under Article 246 of the Chinese Penal Code.Footnote 56 Moreover, in recognition of the special nature of online information dissemination, the judicial interpretation also states that the defamation would be considered to be ‘serious’, if the information is clicked or browsed more than 5,000 times or forwarded more than 500 times.Footnote 57 In 2015, the Penal Code was also amended to add an additional clause in Article 291, which makes it an offence to fabricate information about natural disasters or crime and spread them online, or to spread such false information knowingly online. The issue was finally sealed when the new 2017 Cyber Security Law expanded the liability for prohibited online content from organizations to individuals, which was repeated in two separate provisions (Articles 12 and 48).
One could argue that such draconian laws on netizens are rather unnecessary, especially considering the fact that, unlike the United States, the Internet information service providers are directly liable for the contents generated by users. Under the 2000 Administrative Measures, for example, the Internet information service providers are required, upon discovering prohibited information on their website, to stop the transmission, keep relevant records, and report to the relevant state authorities.Footnote 58 To give real teeth to the requirement, Article 23 of the Administrative Measures also stipulates that Internet information service providers found in violation could have their licences revoked and websites shut down.Footnote 59
The liability for Internet information service providers was duly copied in the Cybersecurity Law.Footnote 60 Moreover, it went one step further by requiring Internet information service providers to establish mechanism to facilitate online complaints and reports.Footnote 61 A dedicated hotline and website (www.12377.cn) were also set up to handle reports on ‘illegal and unhealthy information’, with the first category being ‘political information’.Footnote 62 In 2018 and 2019, between ten million and thirty million reports were made on average every month, with the majority being directed against major social media sites, such as Weibo, Tencent and search engines, such as Baidu.Footnote 63
Another innovation in the Cybersecurity Law is the shift from the regulation of content to requirements on where such content, or data, shall be stored. According to Article 37, operators of critical information infrastructure are required to locally store personal information and important data collected and generated in their operations within China. If they need to send such data abroad due to business necessity, they have to first undergo security assessment by the authorities. This provision raised several concerns. First is what constitutes ‘critical information infrastructure’. Article 31 defines this as infrastructure in ‘important industries and fields such as public communications and information services, energy, transport, water conservancy, finance, public services and e-government affairs’, as well as such ‘that will result in serious damage to state security, the national economy and the people’s livelihood and public interest if it is destroyed, loses functions or encounters data leakage’. Such a broad definition could potentially capture everything and is not really helpful nor does it give much guidance, which is why the same article also directs the State Council to develop the ‘specific scope of critical information infrastructure’.
In 2016, the CAC issued the National Network Security Inspection Operation ManualFootnote 64 and the Guide on the Determination of Critical Information Infrastructure,Footnote 65 which clarified the scope of critical information infrastructure by grouping them into three categories: (i) websites, which includes websites of government and party organizations, enterprises and public institutions, and news media; (ii) platforms, which include Internet service platforms for instant messaging, online shopping, online payment, search engines, emails, online forum, maps, and audio video; and (iii) production operations, which include office and business systems, industrial control systems, big data centres, cloud computing and TV broadcasting systems.
The CAC also laid down three steps in determining the critical information infrastructure, which starts with the identification of the critical operation, then continues with the determination of the information system or industrial control system supporting such critical operation, and concludes with the final determination based on the level of the critical operations’ reliance on such systems and possible damages resulting from security breaches in these systems. More specifically, they listed eleven sectors, which include energy, finance, transportation, hydraulics, medical, environmental protection, industrial manufacturing, utilities, telecom and Internet, radio and TV, and government agencies. The detailed criteria are both quantitative and qualitative. For example, on the one hand, critical information infrastructure includes websites with daily visitor counts of more than one million people and platforms with more than ten million registered users or more than one million daily active users, or daily transaction value of ten million RMB. On the other hand, even those that do not meet the quantitative criterion could be deemed to be critical information infrastructure if there are risks of security breaches that would lead to leakage of sensitive information about firms or enterprises, or leakage of fundamental national data on geology, population and resources, or seriously harming the image of the government or social order, or national security. The potentially wide reach of the criteria was well illustrated by the case of the BGI Group, which was fined by the Ministry of Science and Technology in October 2018 for exporting certain human genome information abroad via the Internet without authorization.Footnote 66 Given the nature of their business, the BGI case could fall under the category of ‘leakage of fundamental national data on … population’, as mentioned earlier.
4 Summary
From the discussion on the remarkable evolution of Internet regulation in China over the past twenty-five years, we can distil two key trends: First, in terms of the institutional framework, we have seen the development from the period of no man’s land in the 1990s to the period of proliferation of regulation and regulators with overlapping and competing jurisdictions in the first decade of the new century. Since the beginning of the current decade, however, we have seen the power of Internet regulation consolidated under the CAC, which emerged as the dominating agency presiding over the troika of Internet governance, with the MIIT and MPS playing supporting roles. Second, in terms of the substantive regulations, we have not only seen the initial gaps in the regulatory landscape being filled with more and more detailed regulation, but also the shift in the regulatory focus. At first, the regulations focused on the technology, or the hardware of the Internet. Gradually, however, the focus shifted to the software, and then to the content, and now even to the data. This moves the regulations closer and closer to the heart of the matter, as the Internet, at the end of the day, is nothing but strings of zeros and ones arranged in specific sequences. With the adoption of the Cybersecurity Law in 2016, the focus has now been shifted to security, as the Internet is increasingly regarded as the key challenge to the all-powerful control of the Party. Thus, for China, Internet or data regulation has been presently elevated to a matter of national security. To put it in the words of President Xi, ‘there is no national security without cybersecurity’.Footnote 67 Moreover, he even linked the survival of the Party with the Internet, by solemnly warning in 2013 that ‘unless we solve the challenge of the Internet, the Party cannot stay in power indefinitely’.Footnote 68 The key to understand data regulation in China, therefore, must be ‘security’. The heightened link with security not only explains the domestic regulatory framework in China but also informs how China would deal with the issue at the international level.
C Trade Agreements
Ever since the Declaration on Global Electronic Commerce at the Second WTO Ministerial Conference in May 1998, WTO members have been exploring ways to incorporate Internet and data regulation into trade agreements.Footnote 69 While not much success was made in the WTO collectively, individual members were able to address the issue in other fora such as free trade agreements (FTAs) and the plurilateral Trade in Services Agreement (TiSA) initiative.Footnote 70 It makes good sense to address the issue in international trade agreements, as the Internet was born with an international nature and closely linked to commerce. At the same time, however, a country’s position on Internet and data regulation in trade agreements is often heavily influenced by its domestic regulatory approach, and China is no exception.
In a way, China’s first encounter with data regulation in the WTO started on the wrong foot as it concerned a sensitive area: China’s regulation of publications and audio-visual products.Footnote 71 In the case, the United States complained that China has failed to grant foreign firms the right to import and distribute publication and audio-visual products. One of the key issues in the case was whether China’s commitments on ‘sound recording distribution services’ cover ‘electronic distribution of sound recordings’, as alleged by the United States.Footnote 72 China disagreed with the US approach and argued instead that such electronic distribution ‘in fact corresponds to network music services’,Footnote 73 which only emerged in 2001 and were completely different in kind from the ‘sound recording distribution services’. According to China, the most fundamental difference between the two is that, unlike ‘traditional’ sound recording distribution services, network music services ‘do not supply the users with sound recordings in physical form, but supply them with the right to use a musical content’.Footnote 74 In response, the United States cited the panel’s statement in US – GamblingFootnote 75 that ‘the GATS does not limit the various technologically possible means of delivery under mode 1’, as well as the principle of ‘technological neutrality’ mentioned in the Work Programme on Electronic Commerce – Progress Report to the General Council,Footnote 76 and argued that electronic distribution is merely a means of delivery rather than a new type of service.Footnote 77 Furthermore, the United States argued that the term ‘distribution’ encompasses not only the distribution of goods, but also distribution of services.Footnote 78 After a lengthy discussion covering the ordinary meaning, the context, the provisions of the GATS, the object and purpose and various supplementary means of interpretation, the panel concluded that the term ‘sound recording distribution services’ does extend to distribution of sound recording through electronic means.Footnote 79 China appealed the panel’s findings, but they were upheld by the Appellate Body, which largely adopted the panel’s reasoning.Footnote 80
The case was also the first WTO case concerning China’s censorship regime. It is interesting to note, however, that the United States did not challenge the censorship regime per se.Footnote 81 Instead, the United States only challenged the alleged discrimination in the operation of the regime, where imported products were subject to more burdensome content review requirements.Footnote 82 Ironically, the United States even proposed, as the solution to the alleged discrimination, that the Chinese Government itself shall shoulder the sole responsibility for conducting content review, rather than outsourcing it to importing firms.Footnote 83
With such an unpleasant experience, China took a cautious approach on the inclusion of Internet or data regulation in other trade fora. While it has signed more than a dozen FTAs so far, most of them have not included provisions on such regulations. The only exceptions are the two FTAs China signed with South Korea and AustraliaFootnote 84 in 2015 and the amendment of the FTA signed with Chile in 2018, which include stand-alone chapters on e-commerce. However, unlike the US FTAs, which often include provisions on free flow of data and ban on data localization requirements,Footnote 85 the earlier mentioned FTAs only address e-commerce-related issues, such as the moratorium on customs duties on electronic transmissions; electronic authentication and electronic signatures; protection of personal information in e-commerce; and paperless trading.Footnote 86 Thus, they do not really address Internet and data regulation issues as such.
A similar approach is taken by China in the WTO negotiations. Even though the United States has long been calling for rules on issues such as free cross-border data flow and ban on data localization requirements, China has ignored these issues until very recently. For example, in its communication on e-commerce jointly tabled with Pakistan before the Eleventh Ministerial Conference, China focused only on ‘cross-border trade in goods enabled by Internet, together with services directly supporting such trade in goods, such as payment and logistics services’.Footnote 87 As I have mentioned in another article, this approach is a reflection of the nature of business of most Chinese Internet firms, as they tend to focus on trade in physical goods facilitated by the Internet, rather than digital products like Google and Netflix.Footnote 88 Thus, when over seventy WTO members issued a joint statement on launching the negotiations on e-commerce at the Eleventh Ministerial Conference in December 2017,Footnote 89 China declined to join. When these members decided to formally launch the e-commerce negotiations in January 2019, however, China changed its position and jumped on the negotiation.Footnote 90 In April 2019, China issued a communication on the joint statement negotiation, in which it repeated the focus on cross-border trade in goods enabled by the Internet.Footnote 91 At the same time, however, it also addressed the main concerns of the United States, including data flows, data storage and treatment of digital products, in the following manner.
First, rather than ignoring these issues as it has done in the past, China chose to face them and acknowledge them as issues of concern for some members. This itself is a positive sign, as it indicates China’s willingness to engage on these issues. Second, at the same time, China also indicated that it was not ready to discuss these issues, at least not in the early stages of the negotiation. Citing the ‘complexity and sensitivity’ of these issues, as well as ‘the vastly divergent views among the Members’, China stated that ‘more exploratory discussions are needed before bringing such issues to the WTO negotiation, so as to allow Members to fully understand their implications and impacts, as well as related challenges and opportunities’.Footnote 92 Such approach is all too familiar to those who follow WTO negotiations closely, as it is basically a polite way of saying ‘we do not want to discuss these issues now’.
Third, in particular, China singled out the issue of cross-border data flows, by stating that ‘[i]t’s undeniable that trade-related aspects of data flows are of great importance to trade development’.Footnote 93 Interesting to note is, however, what China did and did not say in this sentence. It did not, for example, use ‘free flow of data’, which is how the United States has always referred to the issue in its submissions.Footnote 94 On the other hand, it qualified ‘data flow’ with ‘trade-related aspects’. This implies that China is not willing to address all kinds of data flows, just those related to trade. In other words, to the extent that some data flows do not have a trade nexus, they could be legitimately excluded. As I have mentioned elsewhere, this qualification could have wide implications, as it could be employed to justify restrictions on data flows in sectors that China has not made commitments, or even for those covered by existing commitments but provided free of charge (such as Google’s search engine services), as they are not ‘traded’.Footnote 95
Fourth, in an effort to turn the table, China also prefaced the discussion on these ‘other issues’ with the recognition that members shall have the ‘legitimate right to adopt regulatory measures in order to achieve reasonable public policy objectives’. This language is reminiscent of the calls for more ‘policy space’, a term often employed in trade negotiations to justify special and differential treatment and resorting to exceptions clauses. As the China – Publications and Audiovisual case mentioned earlier has illustrated, China will, most likely, invoke the public order exception contained in the general exceptions clauses of both the GATT and GATS to justify its online censorship regime. In particular, regarding data flows, China emphasized that it ‘should be subject to the precondition of security’ and should ‘flow orderly in compliance with Members’ respective laws and regulations’. This extends China’s domestic narrative of cybersecurity to the international level, which is made complete with the earlier reference for all members to ‘respect the Internet sovereignty’ of other members. By elevating the issue to one of ‘sovereignty’, China has shown the seriousness it attaches to the issue of regulating data flow.
In summary, China has made it clear that it is not yet ready to discuss these sensitive data-related issues, at least not in the early stages of the negotiations. There is a possibility that it will consider some of them further down the road, but such negotiations will not be easy given China’s guarded position.
D Conclusion
When people discuss data regulations today, they tend to focus on two main players: the UnitedStates, which calls for free flow of data to serve the interests of firms, and the EU, which prioritizes the need for the protection of personal information and privacy of the consumers. This chapter discusses the third major player – China – which emphasizes data security and even regards it as a matter of national sovereignty. Of course, such a regulatory approach was not formed overnight. Instead, the earlier discussions have illustrated how data regulation with Chinese characteristics has evolved over the past twenty-five years. More specifically, the analyses in this chapter have shown the differing regulatory logics and approaches at two different levels – the national and the international.
First, at the domestic level, we have seen Internet regulation shifting from hardware to software, and now to content and data. The shift in regulatory focus closely follows the development of the Internet in China, where it started as a novelty that was confined to the ranks of tech-savvy geeks, then gradually expanded to the masses with the proliferation of software and apps catered to popular uses, and now permeates everyone’s daily life from socializing and shopping to entertainment and education. Recognizing the central role played by the Internet in modern life, Chinese regulators have shrewdly chosen to regulate data, which is the essence of cyberspace that powers everything, especially with the rise of big data and artificial intelligence. Moreover, data regulation has now been elevated to the level of national security, and the agency that is responsible for content regulation, the CAC, has also evolved into the super-agency that is almost synonymous with data regulation in China. The CAC has no responsibility in promoting the growth of the sector. Instead, its only responsibility is making sure that the cyberspace is secure and nothing unexpected pops up. It is this single-minded pursuit of security that has led to such draconian policies as Internet blockage, filtering and other restrictions on the free flow of data, forced data localization requirements and the transfer of source code. As the Internet is becoming more complicated and omnipotent, we can only expect Internet and data regulations in China to become more sophisticated and omnipresent.
Second, at the international level, due to its unpleasant experience in WTO disputes, China has for a long time been rather cautious in addressing Internet and data related issues. This approach is also reflected in its free trade agreements, which tend to avoid the Internet-related issues. Even though its most recent FTAs – especially the ones with South Korea, Australia and Chile – started to address them, they tend to focus on only e-commerce-related issues and do not really address data flows. At the same time, in contrast to its defensive position on data-related issues, China has been quite aggressive in pushing for liberalization of ‘cross-border trade in goods enabled by Internet’. This reflects China’s interest as the leading goods exporter and the success of its e-commerce platforms such as Alibaba. In its latest proposal on the WTO Joint Statement Initiative on e-commerce, China started to address data regulations, but they were framed as secondary issues that require ‘more exploratory discussions’ and are subject to each member’s ‘right to regulate’ to achieve other policy goals, especially security.
The growth of the Internet in China over the past twenty-five years has not only led to the phenomenal growth of its e-commerce market, but also gave China the confidence and power to export its model, and to ‘set the agenda and make rules for cyberspace at the international stage’, as per the high-level exhortation by President Xi at the Politburo’s Thirty-Sixth Collective Study Session on ‘Implementation of the Internet Power Strategy’ in October 2016.Footnote 96 The success of China’s e-commerce sector will make the Chinese model attractive to many developing countries, as many of them are trying to emulate the accomplishments of China. However, an argument could be made that given China’s huge population base and the resulting enormous market, its e-commerce success story is more ‘in spite of’, rather than ‘because of’, the tight grip on cyberspace by the government. Nonetheless, given China’s growing economic clout, data regulation with Chinese characteristics is something that the rest of the world must grapple with for some time to come. It is in this regard that this chapter tries to make a distinct contribution by offering a preliminary peek behind the cyber curtain, while also offering some hints on the things to come.
A Introduction
In the past two decades, the rapid development of the Internet allowed the growth of e-commerce, and together with the new digital technologies and the Internet of Things, the flow of data – both commercial and personal has increased to levels unseen before. Traditional trade rules could serve as a starting point to deal with these issues but they clearly are not enough. To provide some context, in 1994 – at the time the World Trade Organization (WTO) and its agreements were established by the Marrakesh Agreement – Mosaic was the most used web browser on the Internet. (Netscape Navigator was created the same year, and Internet Explorer was only released in 1995.)Footnote 1 Neither Google, nor Amazon or Facebook existed in 1994. The ‘modern’ rules of trade law were not designed having taken into account the characteristics of contemporary digital trade and data flows.
This situation has led to the regulation of electronic commerce today becoming one of the most important topics in trade law and policy. Efforts of dealing with these issues at a multilateral level started in 1998, when the WTO established a work programme on electronic commerce and at the ministerial conference that same year, members agreed on a temporary duty-free moratorium on all electronic transactions – a practice that since then has been renewed at each WTO ministerial conference.Footnote 2 Further development has been slow paced and we are still far from achieving consensus on this topic. Only in December 2017, forty-four WTO members made a joint declaration to initiate exploratory work together toward future negotiations on trade-related aspects of electronic commerce.Footnote 3 In 2019, some countries like India and South Africa argued that the e-commerce moratorium in the WTO led to loss of revenue, as it gave such transmissions immunity from taxation, and initially opposed to the renewal of the duty-free moratorium.Footnote 4 And while there has been a new reinvigoration under the 2019 Joint Statement Initiative with currently seventy-seven WTO members on board, overall, until now, the WTO has made no substantive progress on e-commerce, and countries have not been able to agree on a multilateral regime for the treatment of e-commerce and data flows.Footnote 5
But the lack of consensus at a multilateral level does not mean that rules for digital trade are not being created elsewhere. In fact, since the beginning of the twenty-first century, certain countries have been including provisions and even chapters on electronic commerce, as well as rules on data flows, in preferential trade agreements (PTAs). It is well known that the United States has been important in the creation and diffusion of digital trade rules, especially after the 2002 US Digital Trade Agenda and the Bipartisan Trade Promotion Authority Act of the same year.Footnote 6 Not so well known is the relevant role other actors have played in the development of these rules.Footnote 7 This contribution focuses on one group of countries of the Latin American region, which have been the most important vectors of the inclusion of e-commerce and data rules in PTAs – a group that includes Chile, Colombia, Mexico, Peru, and Panama. For the purpose of this chapter, we consider ‘Latin American’ PTAs those trade agreements in which at least one, or more parties, is a country from Latin America and the Caribbean region.
Besides highlighting the contribution that those countries have had in the creation and diffusion of this new rule-making, our goal is also to determine the level of regulatory convergence that Latin American countries (LACs) have on rules on digital trade and data flows. For this purpose, we understand regulatory convergence as an overarching notion that aims to reduce unnecessary regulatory incompatibilities between countries in a dynamic and incomplete process.Footnote 8 The rationale behind regulatory convergence in PTAs stems from the idea that regulatory diversity may entail significant costs that can hinder cross-border exchanges,Footnote 9 and that the maintenance of needlessly burdensome cross-border differences in regulation can result in a number of additional negative policy impacts, including higher transaction costs stemming from information asymmetries.Footnote 10 Divergent regulatory requirements can lead to duplication of procedures and costs in trade that are important for all internationally active businesses and especially so for small- or medium-sized enterprises (SMEs), for which such fixed costs can be a deciding factor in whether or not to export or invest, including across borders.Footnote 11 Lack of transparency or clarity of regulations, as well as excessive, inefficient, or ineffective regulations, create unnecessary delays or impose costs on traders and investors.Footnote 12
Regulatory convergence mechanisms include substantive or procedural aspects that are aimed at two different types of regulatory outcomes. In some agreements, regulatory convergence aims to achieve substantive regulatory harmonisation (similar or equivalent regulation – ‘substantive convergence’). Other agreements consider harmonisation of the processes by which regulations are developed, adopted, publicised, and implemented (similar or equivalent procedures – ‘procedural convergence’). With different denominations,Footnote 13 both approaches are present in the PTAs examined in this chapter.
The chapter is organised as follows. After the introduction, we provide a detailed description of e-commerce and data rules found in Latin American PTAs, and their convergence or divergence. Then we briefly present the domestic frameworks of relevant LACs on digital trade–related topics, as well as their consistency with existing international commitments, with special emphasis on personal data protection. To conclude, we highlight some potential conflicts that could arise between these countries’ domestic regulations and international commitments in the field.
B Regulatory Convergence in E-Commerce and Data Flow Provisions in Latin American PTAs
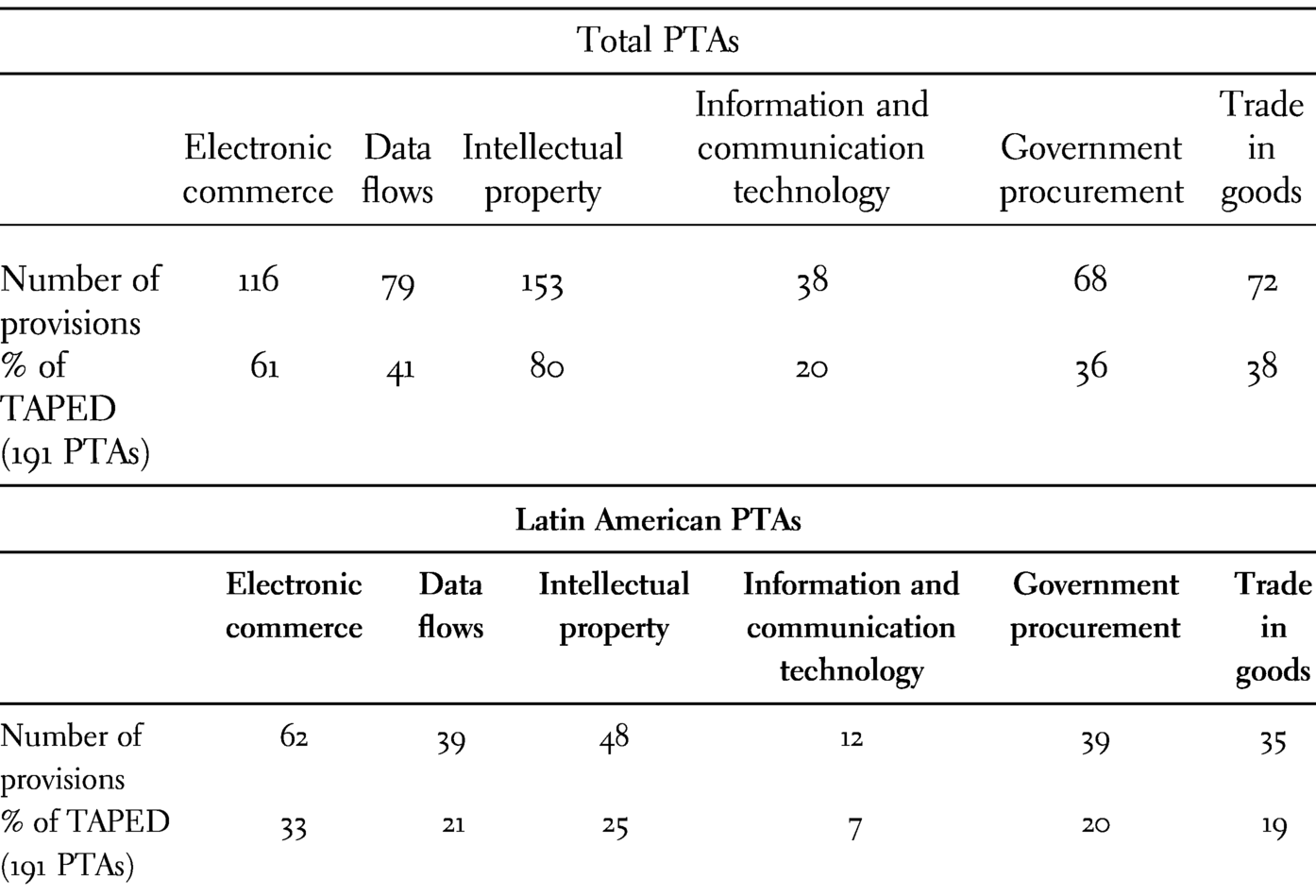
The inclusion of provisions in PTAs referring explicitly to e-commerce and data flows is not a recent phenomenon, although it has evolved importantly in the past two decades. According to the TAPED dataset, 191 PTAs include provisions that are related to e-commerce and data flows, with 116 PTAs with e-commerce provisions and 86 with e-commerce chapters.Footnote 14 These provisions are highly heterogeneous and address various issues including customs duties and non-discriminatory treatment of digital products, electronic signatures, paperless trading, unsolicited electronic messages, as well as consumer protection, data protection, data flows, and data localisation.
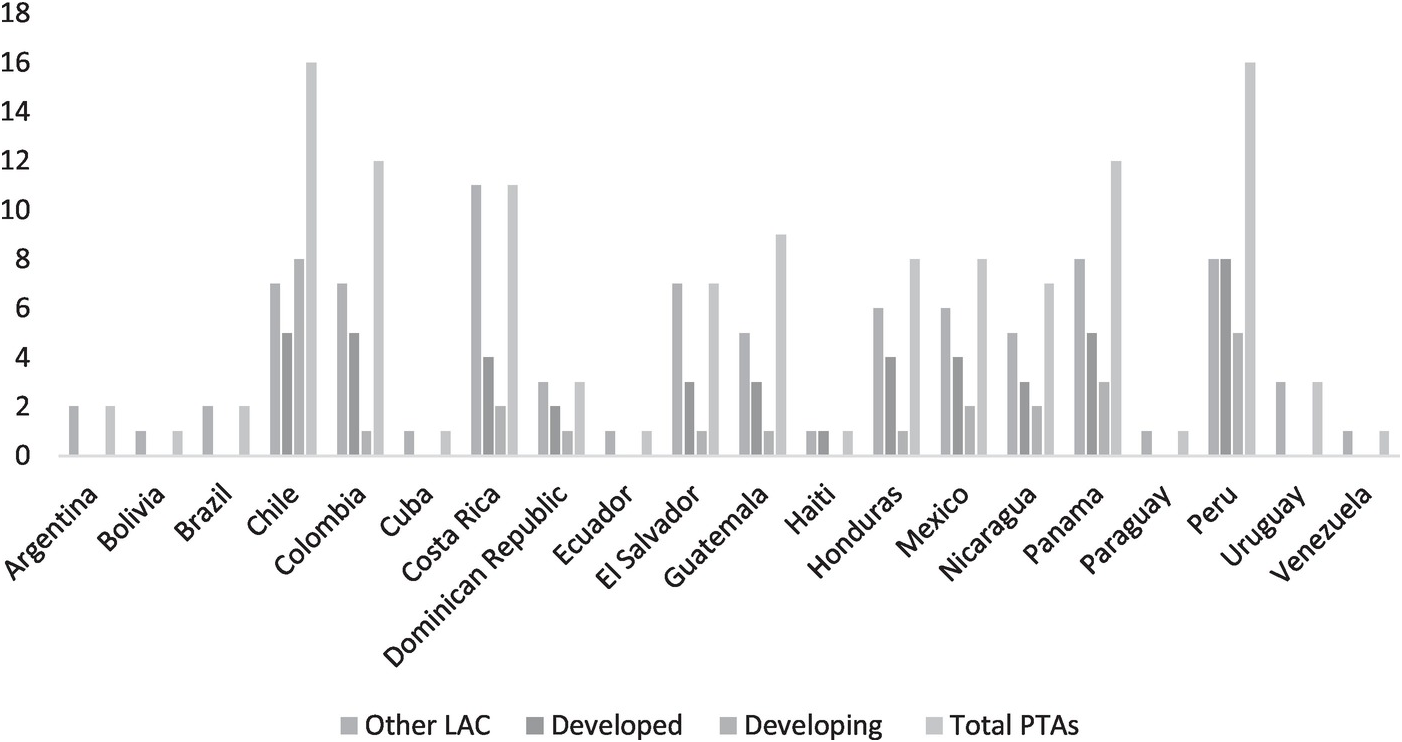
As detailed in Table 13.1, of the total number of PTAs with e-commerce and data flow provisions the countries of Latin America have concluded 53 per cent (62 agreements, 47 chapters). Twenty-nine of these agreements have been concluded with developed countries (47 per cent of this subset) and 33 with other developing countries (53 per cent of this subset), most of them also from Latin America (26 agreements in total). The countries leading this treaty-making practice in the region are Chile (18 PTAs) Peru (16 PTAs), Colombia (12 PTAs), Panama and Costa Rica (11 PTAs each). This is in line with the fact that the surge of PTAs having e-commerce provisions involves both developed and developing countries. 49 per cent of the PTAs with e-commerce provisions were negotiated between developed and developing countries, and 47 per cent were negotiated between developing countries.Footnote 15
Table 13.1. Latin American PTAs with e-commerce or data flow provisions
| Country | Other LACs | Developed | Developing | Total PTAs |
|---|---|---|---|---|
| Argentina | 2 | 1 | 0 | 3 |
| Bolivia | 1 | 0 | 0 | 1 |
| Brazil | 2 | 1 | 0 | 3 |
| Chile | 7 | 5 | 8 | 16 |
| Colombia | 7 | 5 | 1 | 12 |
| Cuba | 1 | 0 | 0 | 1 |
| Costa Rica | 11 | 4 | 2 | 11 |
| Dominican Republic | 3 | 2 | 1 | 3 |
| Ecuador | 1 | 0 | 0 | 1 |
| El Salvador | 7 | 3 | 1 | 7 |
| Guatemala | 5 | 3 | 1 | 9 |
| Haiti | 1 | 1 | 0 | 1 |
| Honduras | 6 | 4 | 1 | 8 |
| Mexico | 6 | 5 | 2 | 9 |
| Nicaragua | 5 | 3 | 2 | 7 |
| Panama | 8 | 5 | 3 | 12 |
| Paraguay | 1 | 1 | 0 | 2 |
| Peru | 8 | 8 | 5 | 16 |
| Uruguay | 3 | 1 | 0 | 4 |
| Venezuela | 1 | 0 | 0 | 1 |
The earliest e-commerce provision in a PTA involving a Latin American country is found in the 2001 Canada–Costa Rica Free Trade Agreement (FTA), which included a Joint Statement on Global Electronic Commerce. In a non-binding fashion, it addresses several issues, like the applicability of WTO rules to e-commerce, supporting industry developments in the field, stakeholder’s participation, transparency, and consumer and data protection. In 2002, the Chile–EU Association Agreement properly included e-commerce provisions in the text of the treaty on issues such as cooperation and data protection.Footnote 16 The first PTA concluded in the region having a dedicated e-commerce chapter is the 2002 Chile–US FTA. In 2006, the Nicaragua–Taiwan FTA began the inclusion of provisions on data flows as part of its cooperation commitments. The number of Latin American PTAs with such provisions has increased over the years (see Figure 13.1), simultaneously with the growing discussions on the digital economy and its move up as a topic on the policy agendas and negotiation tables.
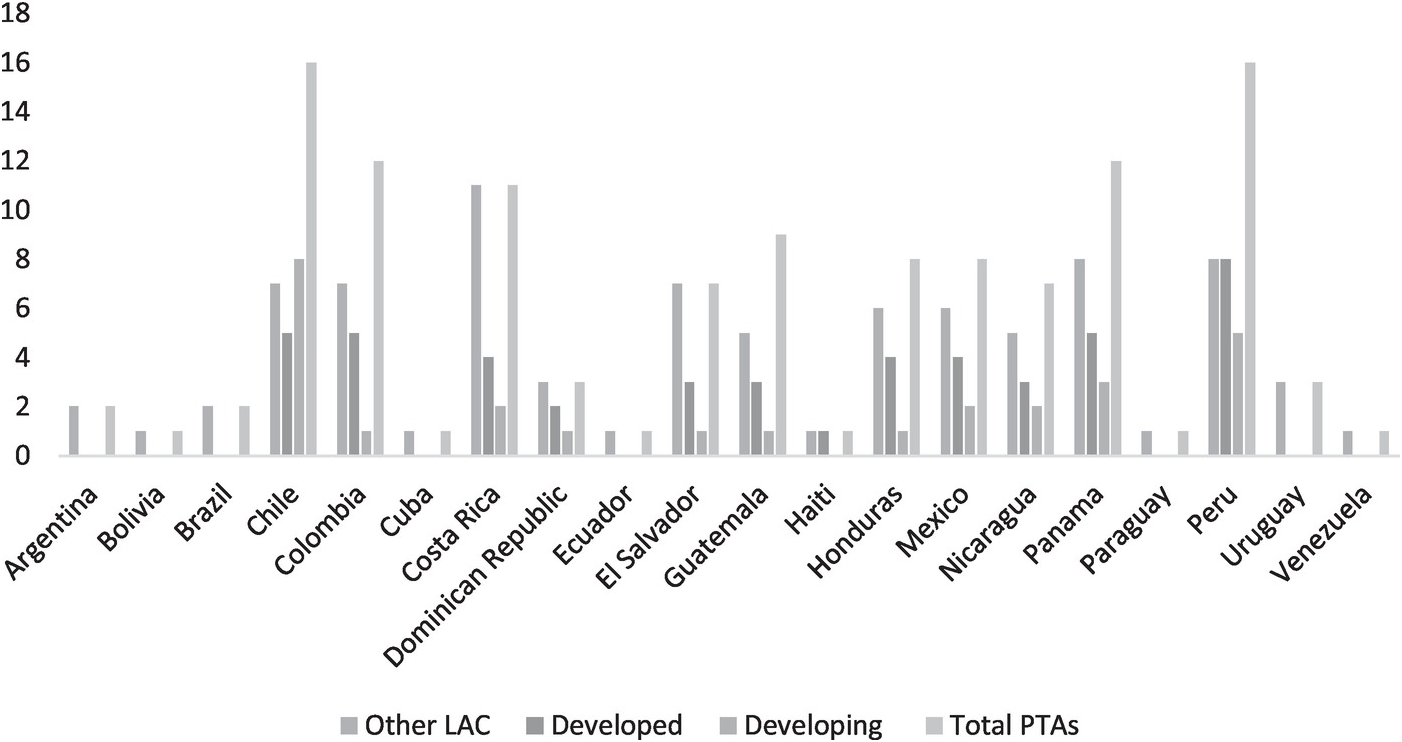
Figure 13.1. Latin American PTAs with e-commerce and data flow provisions
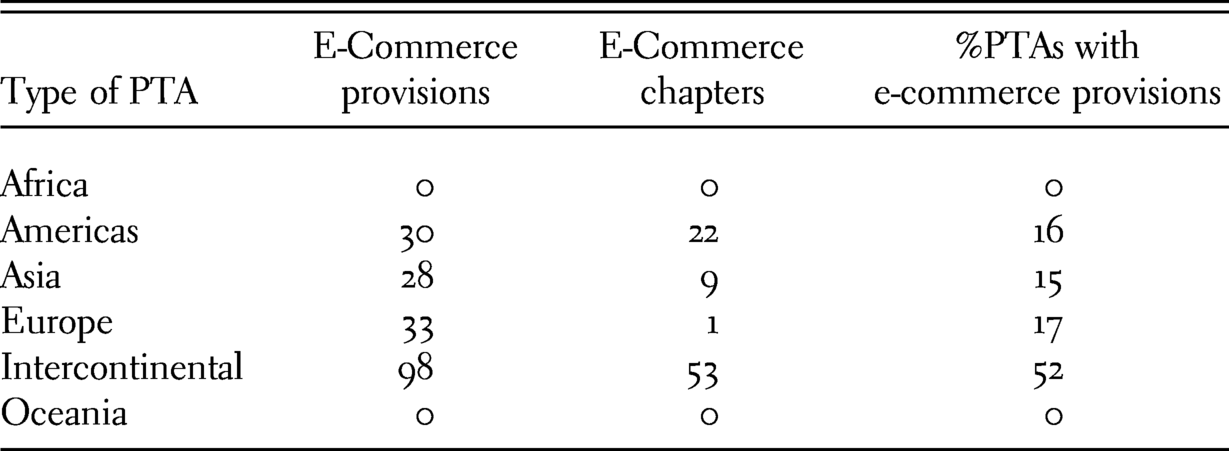
Although the number of PTAs with e-commerce and data flow provisions remains limited, the last eight years have shown a significant increase in the number of agreements with such provisions. Overall, agreements including such provisions are mainly of an intercontinental nature, but around one-third of these PTAs have at least one Latin American country as a contracting party (thirty-one treaties) and Latin America is one of the most relevant regional area with this type of treaty-making (Table 13.2).
Table 13.2. PTAs concluded with e-commerce provisions per region
| Type of PTA | E-Commerce provisions | E-Commerce chapters | %PTAs with e-commerce provisions |
|---|---|---|---|
| Africa | 0 | 0 | 0 |
| Americas | 30 | 22 | 16 |
| Asia | 28 | 9 | 15 |
| Europe | 33 | 1 | 17 |
| Intercontinental | 98 | 53 | 52 |
| Oceania | 0 | 0 | 0 |
PTAs with e-commerce provisions involving LACs have also increased their level of detail significantly over the years. Seven is the average number of PTA provisions found on e-commerce chapters in the past five years, with an average of 955 words. A treaty involving a Latin American country, the United States–Mexico–Canada Agreement (USMCA), is currently the PTA in force with the largest number of articles and words on e-commerce, as its current text has 19 articles and an average of 3,206 words. Several PTAs having a Latin American country as a party have devoted more than 11 articles and 1,900 words to these topics, like the 2017 Argentina–Chile FTA, the 2015 Pacific Alliance Additional Protocol (PAAP), the 2016 Chile–Uruguay FTA, the 2018 Australia–Peru FTA, the 2018 Brazil–Chile FTA, and both the Trans-Pacific Partnership Agreement (TPP) and the Comprehensive and Progressive Agreement for Trans-Pacific Partnership (CPTPP), whose e-commerce chapter reiterates verbatim the TPP text.
C E-Commerce and Data Provisions in Latin American PTAs
E-commerce and data provisions are found in the main text of several Latin American PTAs, mostly on chapters or sections dedicated to e-commerce or intellectual property (IP). When available, data flow provisions are also found in these chapters or sections, but are commonly included in chapters on specific services, mainly telecommunication and financial services. E-commerce provisions can also be found in side documents, like annexes, joint statements, and side letters. As presented in Table 13.3, Latin American PTAs represent an important number of treaties with such provisions.
Table 13.3. Total PTAs and Latin American PTAs with e-commerce and data flow provisions
| Total PTAs | ||||||
|---|---|---|---|---|---|---|
| Electronic commerce | Data flows | Intellectual property | Information and communication technology | Government procurement | Trade in goods | |
| Number of provisions | 116 | 79 | 153 | 38 | 68 | 72 |
| % of TAPED (191 PTAs) | 61 | 41 | 80 | 20 | 36 | 38 |
| Latin American PTAs | ||||||
|---|---|---|---|---|---|---|
| Electronic commerce | Data flows | Intellectual property | Information and communication technology | Government procurement | Trade in goods | |
| Number of provisions | 62 | 39 | 48 | 12 | 39 | 35 |
| % of TAPED (191 PTAs) | 33 | 21 | 25 | 7 | 20 | 19 |
In the following sections, we examine the provisions of Latin American PTAs in two main groups: (i) electronic commerce and (ii) cross-border data flows.
An assessment of the extent of legalisation of these provisions was also performed, distinguishing between ‘soft’, ‘mixed’, and ‘hard’ commitments. We considered as ‘soft’ those commitments that are not enforceable by the parties, like ‘best efforts’ and cooperation commitments. We classified as ‘hard’ those commitments that oblige a party to comply with a rule or a principle and which are enforceable by another party. Finally, we consider an agreement with ‘mixed’ legalisation if the treaty has both soft and hard commitments. Similarly, we included in this category references to other agreements that are only partially applicable.Footnote 17
I Electronic Commerce
1 Objectives and Principles
Several Latin American PTAs with e-commerce chapters converge on explicitly stating a number of objectives like avoiding unnecessary barriers to e-commerce (37 PTAs), addressing the needs of SMEs (31 PTAs), promoting and facilitating its use (both between the parties and globally (30 PTAs), considering private participation in the development of the regulatory framework for e-commerce (15 PTAs), and the principle of technological neutrality (15 PTAs).Footnote 18 The first three objectives and principles are also commonly found in PTAs with e-commerce chapters concluded by countries outside of Latin America.
2 Applicability of WTO Rules
Although all Latin American countries that have concluded PTAs with e-commerce or data flow provisions are members of the WTO that does not necessarily mean that these countries consider that WTO law applies to digital trade. In fact, only one-third of Latin American PTAs include provisions on the applicability of WTO rules to e-commerce – twenty agreements from a total of sixty-two PTAs – with important differences of language across agreements. The first treaty including such provisions is the 2001 Canada–Costa Rica FTA, which only makes a reference to the maintenance of the WTO practice of not imposing customs duties on electronic transmissions between the parties.Footnote 19 Some treaties explicitly recognise the applicability of the WTO rules to electronic commerce, but without clearly specifying which the applicable provisions would be.Footnote 20 Certain agreements clarify the application of WTO rules to e-commerce ‘to the extent they affect electronic commerce’,Footnote 21 or to measures ‘affecting electronic commerce’.Footnote 22 In other softer variations, countries merely reaffirm their respective commitments under WTO agreements in the respective e-commerce chapter/section.Footnote 23
3 National Treatment (NT) and Most-Favoured Nation (MFN) Obligations
The number of Latin American agreements including provisions with explicit commitments on non-discrimination on digital trade is relatively small. In the TAPED dataset, eighteen PTAs include MFN commitments to give a treatment no less favourable on e-commerce to parties to the treaty than they accord to non-parties; and nineteen PTAs consider NT commitments to give a treatment no less favourable to other parties to the treaty than they accord domestically on e-commerce. In contrast, in the whole TAPED dataset we find thirty-five PTAs with NT and thirty-two with MFN provisions.
The large majority of these provisions are binding.Footnote 24 Following the 2015 Pacific Alliance Additional Protocol (PAAP), some agreements consider NT and MFN together, as part of a general commitment to non-discriminatory treatment of digital products. According to this provision, no party shall accord less favourable treatment to digital products created, produced, published, contracted for, commissioned or first made available on commercial terms in the territory of another party or to digital products of which the author, performer, producer, developer, or owner is a person of another party than it accords to other like digital products.Footnote 25 In certain treaties, a footnote further clarifies that to the extent that a digital product of a non-party is a ‘like digital product’, it will qualify as an ‘other like digital product’.Footnote 26
But the majority of Latin American PTAs consider separate paragraphs for NT and MFN. On national treatment, the most common wording goes back to the 2006 Panama–Singapore FTA, which stipulates that a party
shall not accord less favourable treatment to some digital products than it accords to other like digital products, on the basis that the digital products receiving less favourable treatment are created, produced, published, stored, transmitted, contracted for, commissioned or first made available on commercial terms outside its territory; or the author, performer, producer, developer or distributor is a person of another Party or a non-Party; or so as otherwise to afford protection to other like digital products that are created, produced, published, stored, transmitted, contracted for, commissioned, or first made available on commercial terms in its territory.Footnote 27
A variation of this provision uses ‘may’ instead of ‘shall’, theoretically making the commitment less binding.Footnote 28 Another variation narrows the NT as it only applies to the digitally delivered products associated with the territory of the other party or where the author, performer, producer, developer, or distributor is a person of the other party.Footnote 29 A simpler recognition of NT is found in the Canada–Peru FTA, where the parties merely confirm the application of national treatment for goods to trade conducted by electronic means.Footnote 30
Regarding MFN, some agreements stipulate that a party
shall not accord less favourable treatment to digital products created, produced, published, stored, transmitted, contracted for, commissioned or first made commercially available in the territory of another Party, than it accords to like digital products in the territory of a non-Party. Furthermore, a Party shall not accord less favourable treatment to digital products of which the author, performer, producer, developer or distributor is a person of a non-Party.Footnote 31
A variation of this provision uses ‘may’ instead of ‘shall’, making the commitment less binding.Footnote 32
4 Customs Duties
One of the most common provisions found in PTAs regarding digital trade (eighty-four PTAs in TAPED) is the commitment to not impose customs duties on digital products. Wu points out that this type of provision facilitates commerce in downloadable products, such as software, e-books, music, movies, and other digital media.Footnote 33 Despite being commonplace, these commitments have different wording in how the obligation is drafted. From the thirty-nine Latin American PTAs that include such provision, some agreements merely reaffirm the WTO member’s practice of not imposing customs duties on electronic transmissions,Footnote 34 rather than seeking to expand it towards a WTO-plus obligation. However, the most common approach is a provision including a permanent moratorium on duty-free treatment in the PTA, meaning that no customs duties should be imposed on electronic transmissions and digital products. Yet again, this second type of provision has several variations.
Some agreements plainly stipulate that a party may not apply customs duties on digital products of the other party,Footnote 35 or in more binding terms that it ‘shall not’ impose customs duties on electronic transmissions,Footnote 36 or not apply customs duties, fees, or charges on import or export by electronic means of digital products.Footnote 37 In certain agreements, the parties agree that electronic transmissions shall be considered as the provision of services, which cannot be subject to customs duties.Footnote 38 In other treaties, the parties simply agree not to impose duties on ‘deliveries by electronic means’.Footnote 39
Only a couple of agreements consider this obligation regardless whether the digital products in question are fixed on a carrier medium or transmitted electronically.Footnote 40 In several of these treaties there is an explicit distinction between digital products which are transmitted by electronic means and those whose sale occurs online but who are physically transported over the border. According to these PTAs a party shall not apply customs duties on digital products by electronic transmission, but when these are transmitted physically, the customs value is only limited to the value of the carrier medium and does not include the value of the digital product stored on the carrier medium.Footnote 41 A variation of this provision, usually found in agreements concluded with the United States, uses ‘may’ instead of ‘shall’, theoretically making the commitment less binding.Footnote 42 Certain Latin American PTAs explicitly mention that the moratorium does not extend to internal taxes or other charges. The wording of this exclusion varies across treaties. While some do not prevent a party from imposing an internal tax or charge to digital products delivered or transmitted electronically,Footnote 43 others exclude products imported/exported by electronic transmissions or means,Footnote 44 or content transmitted electronically between a person of one party and a person of the other party.Footnote 45
5 Electronic Authentication
Thirty-seven Latin American PTAs include provisions on electronic authentication, which represent around half of the overall universe of PTAs having these provisions. Typically, they allow authentication technologies and mutual recognition of digital certificates and signatures. While earlier treaties included only best efforts commitments in this field, recent agreements include more binding and mandatory clauses. Fifty per cent of all PTAs including such provisions have been concluded by Latin American countries.
We find the earliest example of soft commitments on electronic authentication back in 2001, when Canada and Costa Rica merely acknowledged the necessity of policies to facilitate the use of technologies for authentication and for the conduct of secure e-commerce.Footnote 46 Other agreements included only cooperation commitments on electronic authentication. These comprise activities to share information and experiences on laws, regulations, and programmes on electronic signaturesFootnote 47 or secure electronic authentication;Footnote 48 and to ‘maintain a dialogue’ on the facilitation of cross-border certification services,Footnote 49 or digital accreditation.Footnote 50
More binding commitments on authentication and digital certificates establish restrictions on legislation, using both negative and positive obligations. According to a first group of agreements, no party may adopt or maintain legislation that (i) prevents or prohibits parties from having the opportunity to prove in court that their electronic transaction complies with any legal requirements with respect to authentication;Footnote 51 or (ii) prohibits parties to an electronic transaction from mutually determining the appropriate authentication methods.Footnote 52 Some of these treaties consider this obligation in more binding terms (‘no Party shall adopt or maintain’).Footnote 53 In a second group of agreements, each party has the positive obligation (‘each Party shall adopt or maintain’) of having domestic legislation for electronic authentication that permits parties to electronic transactions to (i) determine the appropriate authentication technologies and implementation models for their electronic transactions, without limiting the recognition of such technologies and implementation models; and (ii) to have the opportunity to prove in court that their electronic transactions comply with any legal requirements.Footnote 54
Further commitments on electronic signatures establish that neither party may deny the legal validity of a signature solely on the basis that it is in electronic form, either in negative (‘may not maintain’)Footnote 55 or positive terms (‘a Party shall not deny’).Footnote 56 Some agreements include exceptions to these commitments, considering that a party may require that the electronic signatures be certified by an authority or a supplier of certification services accredited under the party’s law or regulations for a particular category of transactions or communications.Footnote 57 In certain cases, it is stipulated that such requirements shall be objective, transparent, and non-discriminatory and relate only to the specific characteristics of the category of transactions concerned.Footnote 58 In other agreements, it is considered that a party may deny the legal validity of an electronic signature under circumstances provided for in its law.Footnote 59
Additional commitments on electronic authentication refer to the recognition of digital certificates, either publicly or privately issued. On public authentication, some agreements consider working towards the recognition of such certificates at a government level, based on internationally accepted standards,Footnote 60 on cooperation mechanisms between the respective national accreditation and digital certification authorities for electronic transactions,Footnote 61 or by mutual recognition agreements on digital/electronic signature.Footnote 62 On private authentication, certain treaties encourage the use of interoperable electronic trust or authentication,Footnote 63 digital certificates in the business sector,Footnote 64 and advanced or qualified certificates.Footnote 65 For that purpose, parties may endeavour to facilitate the procedure of accreditation or recognition of suppliers of certification services.Footnote 66
6 Source Code
Overall, few PTAs include provisions referring to source code (sixteen treaties), but one third of them are concluded by Latin American countries. These clauses are largely binding prohibitions to require the transfer or access to proprietary source code of software, as a condition for the import, distribution, sale, or use of such software.Footnote 67
In the CPTPP, the parties commit to not requiring the transfer of, or access to, source code of software owned by a person of another party, as a condition for the import, distribution, sale, or use of such software, or of products containing such software, in its territory. For these purposes, software is limited to mass market software or products containing such software, and does not include software used for critical infrastructure. However, some exceptions are considered in the same agreement, like the inclusion or implementation of terms and conditions related to the provision of source code in commercially negotiated contracts; a modification of source code necessary for a software to comply with domestic laws or regulations; and requirements that relate to patent applications or granted patents, including any orders made by a judicial authority in relation to patent disputes, subject to safeguards against unauthorised disclosure under the law or practice of a party.Footnote 68
Later treaties have largely followed the CPTPP wording on this topic.Footnote 69 An important variation is found in the USMCA, where the protection given to source code also extends to algorithms expressed in a source code. The agreement includes a broad definition of ‘algorithm’, which is understood as ‘a defined sequence of steps, taken to solve a problem or obtain a result’.Footnote 70 Most importantly, the USMCA considers few exceptions to the protection of source code and related algorithms, being limited to the requirements made by a regulatory body or judicial authority for a specific investigation, inspection, examination enforcement action, or judicial proceeding, subject to safeguards against unauthorised disclosure. Such disclosure shall not be construed to negatively affect software source code’s status as a trade secret, if such a status is claimed by the owner. DEPA also deals with algorithms but concerning products that use cryptography and are designed for commercial applications.Footnote 71
7 Personal Data
The protection of personal data in e-commerce or digital trade chapters of Latin American PTAs usually takes two distinctive paths: while one group of provisions deals with it from the point of view of the protection of privacy as a fundamental right (whether or how data is shared, collected, or stored, and regulatory restrictions), another group of provisions regulates the protection of such data as consumer rights. When included, agreements tend to have both privacy and consumers rights provisions, although with different levels of commitment across treaties. Both consumer protection and privacy rules are similar but different takes on the same issue. As we will see, the most binding provisions are related to privacy and not to consumer protection per se.
Few agreements, but increasing in number in recent years, explicitly exclude from the e-commerce chapter the information held or processed by or on behalf of a party or measures related to such information, including measures related to its collection.Footnote 72 These provisions put states in an asymmetrical position vis-à-vis international traders and investors, as they exclude governmental data collection and processing from the disciplines dealing with the treatment of personal data. Around half of all PTAs having these provisions have been concluded by Latin American countries (Table 13.4).
Table 13.4. Personal data provisions in Latin American PTAs
| Privacy issues | Consumer protection | |
|---|---|---|
| Soft Commitments | 33 | 33 |
| Intermediate Commitments | 34 | 10 |
| Hard Commitments | 22 | 0 |
| Total number of provisions | 44 | 43 |
a Privacy Issues
Fourty-four Latin American PTAs include provisions on privacy, usually under the concept of ‘data protection’. But the way this data is protected varies considerably, a truly mixed bag of binding provisions and non-binding provisions. The 2001 Canada–Costa Rica FTA was the first of these agreements dealing with privacy issues, in a non-binding declaration which is largely programmatic.Footnote 73 Later agreements include international cooperation activities to enhance the security of personal data, like sharing information and experiences on regulations, laws, and programmes on data privacy or data protection,Footnote 74 or on the overall domestic regime for the protection of personal information;Footnote 75 technical assistance in the form of exchange of information and experts or the establishment of joint programmes and projects;Footnote 76 maintaining a dialogueFootnote 77 or hold consultations on matters of data protection;Footnote 78 or in general other cooperation mechanisms to ensure the protection of personal data.Footnote 79
While some Latin American PTAs merely recognise the importance or the benefits of protecting personal information online,Footnote 80 in several treaties, parties specifically commit to adopting or maintaining legislation or regulations that protect personal data or the privacy of users of e-commerce,Footnote 81 in relation to the data’s processing and dissemination,Footnote 82 which may also include administrative measures.Footnote 83 Few agreements consider qualifications to this commitment, like the differences in existing systems for personal data protection,Footnote 84 or are explicit in highlighting the ‘best efforts’ nature of these commitments.Footnote 85
Certain treaties add that when developing online personal data protection standards, each party shall take into account international standardsFootnote 86 as well as criteria or guidelines of relevant international organisations or bodiesFootnote 87 – such as the APEC Privacy Framework and the OECD Recommendation of the Council concerning Guidelines governing the Protection of Privacy and Transborder Flows of Personal Data (2013).Footnote 88 Moreover, in a couple of treaties, the parties commit to publishing information on the protections (regarding personal data) it provides to users of e-commerce,Footnote 89 including how individuals can pursue remedies and how businesses can comply with any legal requirements.Footnote 90
Some agreements put a special emphasis on the transfer of personal data, encouraging the use of encryption or security mechanisms for users’ personal information, and their anonymisation, in cases where said data is provided to third parties, in accordance with the applicable legislation.Footnote 91 Furthermore, in a couple of agreements, parties commit to encouraging the development of mechanisms to promote compatibility between different regimes, recognising that they may take different legal approaches to protect personal information. These may include the recognition of regulatory outcomes, whether accorded autonomously, by mutual arrangement, or in broader international frameworks, and the exchange of information.Footnote 92 The USMCA explicitly recognises that the APEC Cross-Border Privacy Rules system is a valid mechanism to facilitate cross-border information transfers while protecting personal information.Footnote 93
But Latin American PTAs have also used more binding options to protect personal information online. A first option is to consider the protection of the privacy of individuals in relation to the processing and dissemination of personal data, as well as the confidentiality of individual records and accounts, as exception in specific chapters of the agreement, usually on telecommunications (to protect the privacy of non-public personal data of subscribers to public telecommunications services),Footnote 94 and financial services (adopting adequate safeguards for the protection of privacy and fundamental rights while permitting data transfer and processing).Footnote 95 Other agreements merely recognise principles for the collection, processing, and storage of personal data, without developing its content in detail.Footnote 96 The USMCA also acknowledges similar principles and the importance of ensuring compliance with measures to protect personal information and ensuring that any restrictions on cross-border flows of personal information are necessary and proportionate to the risks presented.Footnote 97
A second option focuses on the protection of personal data in specific sectors, like financial services. Some PTAs consider that where the financial information or financial data processing involves personal data, the treatment of such personal data shall be in accordance with the domestic law regulating the protection of such data.Footnote 98 A third option leaves the development of rules on data protection to a treaty body. For example, in the 2012 Colombia–EU–Peru FTA (which now includes Ecuador), the Trade Committee may establish a working group with the task of proposing guidelines and strategies enabling the signatory Andean Countries to become a safe harbour for the protection of personal data. To this end, the working group shall adopt a cooperation agenda that shall define priority aspects for accomplishing that purpose, especially regarding the respective homologation processes of data protection systems.Footnote 99 A fourth option allows countries to adopt ‘appropriate measures’ to ensure the protection of privacy while allowing the free movement of data. For that purpose a criterion of ‘equivalence’ is established, meaning that personal data may be exchanged only where the party that may receive it protects such data in at least an equivalent, similar, or adequate way to the one applicable to that particular case by the party that may supply them. To that end, the parties shall negotiate reciprocal, general, or specific agreements, or in a broader international framework, admitting private sector’s implementation of contracts or self-regulation. Up to now, this option has only been introduced in the 2017 Argentina–Chile FTA.Footnote 100
b Consumer Protection
Overall, forty-three Latin American PTAs include provisions on consumer protection or consumer ‘confidence’, explicitly applicable to e-commerce or digital trade, which are however largely non-binding. The 2001 Canada–Costa Rica FTA recognised that consumers who participate in electronic commerce should be afforded transparent and effective protection that is not less than the level of protection afforded in other forms of commerce.Footnote 101 Later agreements consider international cooperation on consumer protection, like sharing information and experiences on regulations, laws, and programmes,Footnote 102 on means for consumer redress,Footnote 103 or in confidence in e-commerce.Footnote 104 Other activities include the exchange of best practices, information or views on online protection,Footnote 105 or access to products and services offered online;Footnote 106 and maintaining dialogue/consultationsFootnote 107 about the protection in the ambit of electronic commerce,Footnote 108 or especially from fraudulent and misleading commercial practices in the cross-border context.Footnote 109
In the 2014 Pacific Alliance Additional Protocol, the parties agree to a number of additional commitments, including cooperation agreements for the cross-border protection of consumer rights; exchanging information about suppliers sanctioned for infringement of those rights; promote prevention measures and training initiatives on the protection of consumer rights in e-commerce and prevention measures; standardise the information that must be provided to consumers in this environment; and encourage e-commerce suppliers to comply with consumer protection regulations in the territory of the party in which the consumer is located.Footnote 110 Some Latin American PTAs also deal with consumer protection with reference to the adoption of domestic standards, but largely in a non-binding fashion, ‘recognising the importance’ of transparent and effective measures to protect consumers from fraudulent and deceptive commercial practices when they engage in e-commerce.Footnote 111 But in only a handful of agreements do the parties commit to adopting or maintaining consumer protection laws to prescribe these practices when they cause harm or potential harm to consumers.Footnote 112 Certain treaties also recognise the importance of cooperation between the respective national consumer protection agencies on activities related to cross-border electronic commerce,Footnote 113 or exchanging information and experiences in order to enhance consumer protection.Footnote 114 Few agreements consider that the parties may evaluate the use of alternative dispute resolution mechanisms,Footnote 115 or even online dispute settlement for the protection of consumer, if feasible.Footnote 116
But Latin American PTAs have also used more binding options to tackle consumer protection. Some establish a criterion of ‘equivalence’ that each party shall provide, where possible and in a manner considered appropriate, protection for consumers using e-commerce that is at least equivalent to that provided for consumers and other forms of commerce under their respective domestic laws, regulations, and policies.Footnote 117 Furthermore, the 2008 Australia–Chile FTA considers specific businesses obligations to protect consumers in e-commerce, including acting in accordance with fair business, advertising, and marketing practices, like providing accurate, clear, and easily accessible information about goods or services offered; avoiding ambiguity on intent to make a purchase; and provide easy-to-use, secure payment mechanisms and information on the level of security such mechanisms afford.Footnote 118
II Rules on Data
Several Latin American PTAs include general provisions on cross-border flow of data. These are found in both electronic commerce/digital trade chapters, as well as in dedicated chapters of sectors, where data flows play a central role, like telecommunications and financial services. Around half of all FTAs including data flow provisions have been concluded by Latin American countries (Table 13.5).
Table 13.5. Data flow provisions in Latin American PTAs
| Data flows | ||||
|---|---|---|---|---|
| General | Financial services | Telecommunications | Data localisation | |
| Soft Commitments | 6 | 0 | 1 | 1 |
| Intermediate Commitments | 4 | 0 | 0 | 0 |
| Hard Commitments | 8 | 33 | 31 | 8 |
| Total Number of Provisions | 18 | 33 | 32 | 9 |
Two types of data-related provisions are found on Latin American PTAs with e-commerce or digital trade chapters: (i) those referring to cross-border flow of data and (ii) those banning or limiting data localisation requirements, the former being more common, but with different levels of commitments across agreements.
1 Data Flows
There are basically two sets of provisions concerning data flows in Latin American PTAs: one binding, directly guaranteeing the free flow of data, the other non-binding, considering cross-border information flows as part of the cooperation activities between the parties. Few agreements consider some ‘intermediate’ type of clauses, including best endeavour provisions and commitments to future negotiations on data flows. PTAs concluded by Latin American countries are the largest group of trade agreements that include data flow provisions (thirty-nine agreements out of seventy-nine). Non-binding provisions on data flows appeared earlier. The first agreement having this type of provisions is the 2006 Taiwan–Nicaragua FTA, where as part of the cooperation activities, the parties affirmed the importance of working ‘to maintain cross-border flows of information as an essential element to promote a dynamic environment for electronic commerce’.Footnote 119 A similar wording is used in later agreements concluded by Peru, Mexico, Colombia, Costa Rica, and other Central American countries.Footnote 120 An intermediate type of provision is where the parties agree to consider commitments related to cross-border flow of information in future negotiations. This type of clause is found in the 2015 Pacific Alliance Additional ProtocolFootnote 121 and in the Modernisation of the Trade part of the EU–Mexico Global Agreement, currently under negotiation.Footnote 122 In the latter, the parties commit to ‘reassess’, within three years of the entry into force of the agreement, the need for inclusion of provisions on the free flow of data.
The first agreement having a binding provision on cross-border information flows is the 2014 Mexico–Panama FTA. According to this treaty, each party ‘shall allow its persons and the persons of the other Party to transmit electronic information, from and to its territory, when required by said person, in accordance with the applicable legislation on the protection of personal data and taking into consideration international practices’.Footnote 123 A much more detailed provision is found in the 2015 amended version of the PAAP,Footnote 124 which was then included in the 2016 TPP, and the TPP template has largely influenced subsequent agreements with data flow provisions.
After recognising that each party may have its own regulatory requirements concerning the transfer of information by electronic means, both the PAAP and the TPP stipulate that each party shall allow the cross-border transfer of information by electronic means, including personal information, when this activity is for the conduct of the business of a covered person. This shall not prevent a party from adopting or maintaining measures to achieve a legitimate public policy objective, provided that the measure is not applied in a manner which would constitute a means of arbitrary or unjustifiable discrimination or a disguised restriction on trade; and does not impose restrictions on transfers of information greater than are required to achieve the objective. The same provision was kept in the 2018 CPTPP, signed after the withdrawal of the United States from the TPP and in DEPA.Footnote 125
After TPP, a similar hard rule on data flows has been incorporated into other trade agreements concluded by Chile, Argentina, Peru, Mexico, and Brazil, largely following the same wording.Footnote 126 In the 2017 Argentina–Chile FTA, there is a specific reference that the parties undertake to apply to the data received from the other party a level of protection that is at least similar to that applicable to the party from which the data originates, through mutual, general, or specific agreements.Footnote 127 In the USMCA, a footnote clarifies that a measure restricting data flows is not considered to achieve a legitimate public policy objective, if ‘it accords different treatment of data transfers solely on the basis that they are cross-border in a manner that modifies the conditions of competition to the detriment of the service suppliers of the other Party’.Footnote 128
2 Data Localisation
In recent years, some preferential trade agreements have also started to include provisions on data localisation, either banning or limiting such requirements. An important difference with data flow provisions analysed in the previous section is that the large majority of data localisation provisions are of a binding nature. Again, PTAs concluded by Latin American countries are the largest group of trade agreements that include data flow provisions (nine agreements out of seventeen). The 2015 amended version of the Pacific Alliance Protocol includes a provision on the use and location of computer facilities, stipulating that no party may require a covered person to use or locate computer facilities in the territory of that party as a condition for the exercise of its business activity. An exception in this regard considers that nothing shall prevent a party from adopting or maintaining measures to achieve a legitimate public policy objective, provided that such measures are not applied in a manner that constitutes a means of arbitrary or unjustifiable discrimination, or a disguised restriction to trade.Footnote 129
In 2016, the TPP considered largely the same provision on location of computing facilities, requiring in addition that such measures shall not impose restrictions on the use or location of computing facilities greater than are required to achieve the objective. The same provision was kept in the 2018 CPTPP.Footnote 130 A similar hard rule on data localisation largely following the same wording was included in the 2016 Chile–Uruguay FTA and in DEPA.Footnote 131 The 2018 Brazil–Chile FTA has a minor deviation from the TPP drafting, as it does not require that data localisation provisions are the least restrictive measure to achieve the public policy objectives. In this regard, its wording is closer to the PAAP.Footnote 132
A more succinct version of this type of provision is found in the USMCA, which stipulates that no party shall require a covered person to use or locate computing facilities in that party’s territory as a condition for conducting business in that territory, without considering any further exception.Footnote 133 One of the few provisions on data localisation that are not directly binding is found in the 2017 Argentina–Chile FTA. Under this treaty, the parties merely ‘recognise the importance’ of not requiring a person of the other party to use or locate the computer facilities in the territory of that party, as a condition for conducting business in that territory. To this end, the parties undertake to exchange good practices, experiences, and current regulatory frameworks regarding the location of servers.Footnote 134
D Legal Framework of E-Commerce and Personal Data Protection in Latin American Countries
As mentioned, a group of five Latin American countries, Chile, Colombia, Costa Rica, Panama, and Peru, have concluded an important number of trade agreements with clauses or chapters on e-commerce and data flows, representing around half of all the PTAs that include these provisions. In this section we examine whether the domestic legal framework of these countries corresponds to their international commitments, taking as a case study the regulation of data protection.
Most Latin American countries, sharing the tradition of European continental civil law, have recognised the right to the protection of personal data and the right to privacy as separate legal notions. Several Constitutions of the region recognise explicitly the right to privacy, but those of Argentina, Brazil, Colombia, Mexico, Peru, and Venezuela also include the ‘habeas data’, or the right to the protection of personal data. But even in countries where this mechanism is not expressly contained in the Constitution, the relevant courts have recognised the ‘right to control’ personal information.Footnote 135
Chile, Colombia, Costa Rica, Panama, and Peru have also domestic regulations on the processing of personal data in both the public and private sectors. Chile was the first to introduce such framework in 1999, followed by Colombia in 2008.Footnote 136 However, in most of these countries there are concerns on the proactive application of data protection laws and regulations by their respective Data Protection Authority (DPA) – and in some cases such authority does not exist. Other challenges commonly mentioned are the harmonisation of cross-border cooperation for the protection of privacy with other DPAs and police and judicial authorities; the promotion of privacy management programmes including obligations to respond, inform, and compensate data owners in case of violation of security that affects personal information; and the enhancement of interoperability with other regional and national privacy and data protection frameworks.Footnote 137
I Chile
The regulation of electronic commerce in Chile is largely contained in the general domestic legislation (e.g. Code of Commerce, Civil Code). Only in some cases, special norms have been created to respond to the challenges posed by new technologies. In 2002, Chile adopted a law on electronic documents and electronic signature (Law 19,799) which explicitly recognises the legal principles of freedom to provide services, free competition, technological neutrality, international compatibility, and equivalence of electronic support to paper support, meaning that everything contained in electronic format has the same validity as a paper document.Footnote 138 However, self-regulation of e-commerce as a complement of legal norms is still very relevant.Footnote 139
Although rules on the protection of consumer rights were established back in 1997 (Law 19,496), these norms did not refer to e-commerce until 2004, when amendments introduced by the Law 19,955 included explicit provisions to deal with the challenges posed by digital commerce.Footnote 140 In 1999, Chile enacted the oldest personal data protection regulation in the region, the Law 19,628 ‘On the protection of private life’, which include provisions on the treatment of personal information in public and private databases. The law has been amended a couple of times: firstly, forbidding credit risk predictions or assessments that are not based on objective data like late payments of natural or legal persons (Law 20,521 of 2011); and secondly, establishing the principle of finality in the treatment of personal data of economic, banking, financial, or commercial nature (Law 20,575). Some other sectoral laws deal with data protection, like the regulation prohibiting the inclusion of sensitive personal data in ‘active transparency’ public websites (Law 20,285 of 2008); or the law making all information regarding healthcare procedures and treatments sensitive data (Law 20,584 of 2015).Footnote 141
This regulation has been criticised for its lack of enforcement, being outdated and insufficient for the expectations of both private sectors and regulators,Footnote 142 and lacking a specific and independent institution that serves to effectively protect the rights associated with data processing.Footnote 143 In response to those criticisms in June 2018, a Constitutional amendmentFootnote 144 recognised the ‘right to personal data protection’, complementing the protection already granted to private life, as well as the honour of the person and their family.Footnote 145 A bill of law to implement this right that would introduce a data protection system similar to the EU’s General Data Protection Regulation (GDPR) and the creation of a DPA is still under discussion at the Chilean Congress.Footnote 146
None of the existing domestic rules mentioned earlier contain any restrictions on international transfer of data, but the bill of law currently discussed at the Congress includes certain restrictions derived from the express recognition of principles, such as consent, finality (in general terms, not only for the specific sectors mentioned earlier), proportionality, quality, security, liability, and legality of data processing.Footnote 147
II Peru
Peru largely relies on general civil law to address electronic commerce issues, although it has included special provisions on e-commerce in consumer protection laws,Footnote 148 like the ‘Law on Digital Signatures and Certificates’ (Law 27,269 of 2000) which regulates electronic signatures and gives them the same validity and legal effect as handwritten signatures; and the ‘Anti-spam Law’ (Law 28,493 of 2005), which governs the use of non-solicited advertisement e-mailing.Footnote 149
Under the 1993 Peruvian Constitution, everyone has the right that information services, computerised or not, public or private, do not provide information that affects personal and family privacy. Furthermore, the Constitution limits the right to request and receive information from any public entity, in cases where the information affects personal privacy, or those that expressly are excluded by law or for reasons of national security. The Constitution also protects bank secrecy and tax reservation, which can only be lifted at the request of the judge, the National Prosecutor, or a congressional investigative commission in accordance with the law.Footnote 150 The Peruvian Constitution establishes the guarantee of ‘habeas data’ (which proceeds against the acts or omissions, by any authority, official or person that violates or threatens to violate the aforementioned rights).Footnote 151 The proceedings of the habeas data were initially detailed in a separate law (Law 26,301 of 1994), but are now included in the Constitutional Procedural Code (Law 28,237).Footnote 152
Based on the Constitutional provisions referred to earlier, the Personal Data Protection Law (PDLP – Law 29,733 of 2011) specifically protects the use of personal data of any natural person and applies to both private and state entities. In March 2013, the PDLP was complemented by a Regulation (Supreme Decree 003-2013-JUS) that develops, clarifies, and expands its requirements and set forth specific rules, terms, and provisions regarding data protection. Another statute (Law 27,489 of 2001) regulates activities related to risk centres and companies that handle sensitive personal data and information posing higher risks to individuals (like that related to financial, commercial, tax, employment or insurance obligations or background of a natural or legal person that allows evaluating its economic solvency).Footnote 153
Peruvian PDLP was criticised for the lack of a DPA, which was finally created by Legislative Decree 1,357 of 2017. Today, the Directorate for the Protection of Personal Data is the primary agency in charge of enforcing data protection matters, which is part of the General Directorate of Transparency, Access to Public Information and Protection of Personal Data (NDPA). Yet, the fact that the DPA is not autonomous and is under the authority of the Ministry of Justice has been criticised by sectors of the civil society.Footnote 154
The 2017 reform also strengthened the regime for the protection of personal data and the regulation of interest management. According to Article 15 of the Law 29,733 transfers of personal data beyond Peruvian territory require consent from data subjects, and they can only be transferred to jurisdictions with ‘adequate’ levels of data protection,Footnote 155 or to jurisdictions with lower levels, subject to a privacy guarantee from the data controller. However, some transfers of personal data are generally allowed, like those that take place as part of an international treaty on cross-border flow of personal data in which Peru is a party (which would include the PTAs mentioned in the first part of this chapter); international judicial cooperation or among intelligence agencies; those needed to execute a contractual relationship, medical treatment or a scientific or professional relation involving the owner of the personal data subject; and those conducted for bank or stock transfers trading. Notification to the DPA is required for international transfers.Footnote 156
III Panama
Electronic commerce in Panama is governed by the Law 51 of 2008 (amended by Law 82 of 2012), and a couple of Executive Decrees (No. 40 of 2009 and No. 684 of 2013), which regulate the creation, use, and storage of electronic documents and signatures, using a registration process, as well as the supervision of providers of data storage services.Footnote 157 The regulation was based on the 1996 UNCITRAL Model Law on electronic commerce and provides for enforcement through the General Directorate of Electronic Commerce (DGCE).Footnote 158
Until 2018, Panama did not have a law dedicated to the protection of personal data. A bill regulating this issue was introduced in the Congress in August 2018 and approved in October the same year. The Law of Protection of Personal Data (Law 81 of 2019) was promulgated only on 31 March 2019. The new law establishes that the processing of personal data may only be carried out when there is consent of the owner or when the law permits it.Footnote 159 The legislation is applicable to all databasesFootnote 160 containing personal information, whether of nationals or foreigners, who are within the territory of the Republic of Panama or whose data controller is domiciled in the country. The cross-border treatment of personal data originated or stored in Panama that is confidential, sensitive, or restricted is permitted provided that the data controller and the country of destination of the data comply with protection standards that are equal or superior to those indicated in Law 81. However, the same regulation considers several exceptions to this rule – for example, when owners of the data have given their consent for the transfer and cross-border treatment; when the transfer is necessary for the execution, present or future, of a contract in the interest of the owner; when it is related to bank transfers, money, and stock market securities; when it is information required by law under international agreements or treaties signed by Panama.Footnote 161 Law 81 also establishes that those responsible or custodians of a database that transfer personal data to third parties must keep a record of them, which must be available to the newly created National Authority of Transparency and Access to Information (ANTAI), but only in case that such authority would require it. The same law also creates a Council for the Protection of Personal Data, which makes recommendations of public policies and evaluates cases entailing the protection of personal data, and also provides advice to ANTAI.Footnote 162 The actual implementation of this new law is a matter that cannot be ascertained at the moment of this writing.
IV Colombia
The regulation of e-commerce in Colombia is found mainly in Law 527 of 1997 or ‘Electronic Commerce Law’, which establishes the ‘principle of functional equivalence’, between electronic signature and autograph signatures, data messages and written documents, and sets up rules for the certification of digital signatures and for the creation of certification entities. Several additional laws complement this framework on consumer protection, like the Law 1,480 of 2011, which establishes special obligations for suppliers of goods and services that are offered using electronic means like special information duties (identification of provider, characteristics of the goods, means of payment available, contract text, etc.), duties to conserve information, and procedures of filing petitions, complaints, and claims.Footnote 163
The Colombian Constitution recognises two fundamental personal data rights: the right to privacy and the right to data rectification.Footnote 164 Personal data processing is further regulated by two statutory laws and several decrees that set out data protection obligations. The first one, the ‘Habeas Data Law’ (Law 1,266) was enacted in 2008, after intense discussions, and regulates the handling of information contained in some personal databases,Footnote 165 especially of financial, credit, commercial, services data collected in Colombia or abroad.
In 2012, a statutory law for the protection of personal data was enacted (Law 1,581). This statute regulates personal data processing, as well as databases including special rules for sensitive data and data collected from minors. The law further regulates data processing authorisation and procedures, and creates the National Register of Data Bases (NRDB) administered by the Superintendence of Industry and Commerce (SIC, the Colombian DPA). Law 1,581 is applicable to all data collection and processing in Colombia.Footnote 166 Under Article 26 of Law 1,581 of 2012, transfers of private or semi-private personal data must be authorised by data subjects and are not allowed to jurisdictions that the SIC regards as not providing ‘adequate’ levels of management of personal data. It is understood that a country offers an adequate level of data protection when it complies with the standards set by the SIC on the subject, which in no case may be less than those required by the Law 1,581. Exceptionally, beyond those cases, international transfers are allowed for exchange of financial information for transfers and banking operations; for medical, health, and public hygiene reasons; pursuant to international treaties joined by Colombia; for contracts involving the data subject and a counterpart; and when required by public interest.Footnote 167
Despite the existing regulation, it has been criticized that Colombia still does not have successful initiatives that seek to adapt the personal data protection regime to the era of big data and the digital economy. Some scholars find fault with the fact that this law focuses on the protection of commercial and financial data and leaves normative gaps preventing the complete protection of personal data in Colombia.Footnote 168 Others have pointed out that the law is not applicable to those responsible or in charge of data processing that do not reside or are not domiciled in Colombia, even though they perform operations on personal data of persons who reside, are domiciled or located in Colombia.Footnote 169
V Costa Rica
Currently in Costa Rica there is no electronic commerce law or framework that regulates all the essential aspects of online commerce. In 2013, a bill on services for the information society (or ‘Electronic Commerce Law’) was presented to the Legislative Assembly but has not been approved yet.Footnote 170 However, some related laws have already been enacted, such as the Law 8,454 of 2005, of certificates, digital signatures, and electronic documents.Footnote 171 Additionally, in 2017, a reform of the Regulation to the Law of Promotion of Competition and Effective Defence of the Consumer, introduced a new chapter on Consumer Protection in the Context of Electronic Commerce.Footnote 172
Data privacy regulation in Costa Rica is contained in two laws – the Law 7,975 of 2000, ‘Undisclosed Information Law’, which makes it a crime to disclose confidential and/or personal information without authorisation, and the Law 8,968 of 2011 on Protection in the Handling of the Personal Data of Individuals (amended in 2016), which together with its by-laws, regulates the activities of companies that administer databases containing personal information, and recognises the ‘Right to Self-Determination of Information’, which includes access, rectification, cancellation, and opposition to the processing of personal data. The same law created the Agency for the Protection of Data of Inhabitants (PRODHAB), as the DPA and regulatory body of databases and requires the mandatory paid registration of all databases, public or private, for distribution, dissemination or commercialisation purposes.Footnote 173
Concerning transfers of data, Law 8,968 stipulates that controllers of public or private databases can transfer personal data only if the data subject has provided express and valid consent. However, the law is not clear whether this provision relates to transfers within Costa Rica or transfers to a third country.Footnote 174 As a consequence of such unclear regulation, the transfers of personal information from a database to a service supplier, technological intermediary, or entities in the same ‘economic interest group’ are not considered as transfers of personal information and therefore do not need authorisation from the data subject.Footnote 175
The local press has reported that the main weakness in the protection of information is the lack of care for the users when disclosing personal data, without reviewing the conditions of use. Additionally, the lack of registration of private-led databases (despite the fact that is a mandatory procedure) and the lack of adequate human and financial resources of PRODHAB have been criticised.Footnote 176
E Conclusion
As we have seen throughout this chapter, a group of Latin American countries have pioneered the inclusion of e-commerce and data flow provisions in preferential trade agreements. These countries have done so, in a largely consistent way, with an important level of regulatory convergence on certain objectives and principles (like facilitate and promote e-commerce, avoid unnecessary barriers, and address the needs of SMEs), as well as on specific commitments, such as moratorium on custom duties, electronic authentication, source code, consumer protection, personal data, data flows and data localisation, yet, with different levels of legalisation. These principles and commitments were largely developed in the conclusion of PTAs with developed countries.
But Latin American countries have also advanced new principles on e-commerce and data flows in the conclusion of trade agreements. Around half of all PTAs including data flow provisions on telecommunications or financial services have been concluded by Latin American countries, and the 2014 Mexico–Panama FTA was the first PTA with general binding provision on cross-border information flows. Latin American PTAs are the largest group of treaties that include provisions either banning or limiting requirements of data localisation. Additionally, the largest number of agreements including provisions on stakeholder’s participation or the principle of ‘technological neutrality’ has also been concluded by Latin American countries. Only three PTAs explicitly recognise the principle of ‘net neutrality’Footnote 177 and all have been concluded between Latin American countries.Footnote 178
A further testimony to the creative role of Latin American countries on these topics is the announcement made on 18 May 2019 on the side lines of the Asia-Pacific Economic Cooperation (APEC) meeting of Ministers Responsible for Trade in Viña del Mar, Chile, of the start of the negotiations of a Digital Economy Partnership Agreement (DEPA) between Chile, Singapore, and New Zealand.Footnote 179 The agreement was finally concluded on 21 January 2020 covering all aspects of the digital economy to support trade in the digital era, and also going beyond existing commitments, looking at a range of emerging issues, like cross-border data flows, digital identities, artificial intelligence, electronic invoicing, and open government data.
However, the five examined Latin American countries have not all had the same consistency at domestic level, with national regulations on certain topics addressed in PTAs that lag behind what has been committed to in those agreements, particularly on the issue of data protection. The Organization of American States (OAS) has reported that a consistent and coherent regional approach to the protection of personal data has not yet emerged in Latin America. In 2015, the Inter-American Juridical Committee adopted a ‘Proposal for the Declaration of Principles of Privacy and Protection of Personal Data in the Americas’ with the purpose of urging the OAS member states to adopt measures to respect privacy, reputation, and dignity of people in the Americas.Footnote 180 At the same time, a group of five countries of the region that are considered to have a moderate (Chile, Colombia, Costa Rica, Peru) or limited (Panama) data protectionFootnote 181 are leading the conclusion of PTAs including digital trade and data flow provisions. While these provisions are not all binding, general provisions on data flows, as well as on specific sectors (financial services and telecommunications), have become commonplace in recent years. In contrast, data protection provisions in these PTAs are largely non-binding or their scope of application is left to domestic regulations.
The different levels of commitment and approaches on these issues found in these five countries between the international and domestic regulation, as well as their implementation (or lack thereof), potentially create the possibility of future conflicts, if some of these countries intend to change the domestic regime for data protection. If both regimes are not well-coordinated, Latin American countries could be limited in their policy space to enact rules that contradict international commitments. For example, from the group of countries mentioned earlier, only Colombia, Panama, and Peru have established a criterion of equivalence for the international transfer of personal data, meaning that those countries agree that personal data may be exchanged only where the party which may receive them undertakes to protect such data in at least an ‘adequate’ way to the one applicable to the party from where that data originates. In all the PTAs examined in this chapter, we find such a rule only in the 2017 Argentina–Chile FTA.
In several of these countries discussions are taking place to reform data protection laws to a model that is closer to the EU’s GDPR. Up to now, the only Latin American countries the EU has determined as having and adequate levels of data protection under the GDPR are Argentina and Uruguay.Footnote 182 What would happen if other countries of the region made a policy change to be GDPR adequate and implement their own adequacy policies? Could that be a violation of PTA commitments to allow the cross-border transfer of information by electronic means that do not include such exception?Footnote 183 Is this a problem waiting to happen?
A matter for further research is to determine why these Latin American countries have pioneered the development and diffusion of electronic commerce and data flow provisions in PTAs. Is this a sort of path dependency or the influence of third countries, a reaction to particular economic interests, or rather the will to be in a position of rule-makers and not rule-takers?Footnote 184 The answers to these questions could help to shed a light on the development of new rules for digital trade.
A Introduction
Policymakers face a tension between, on the one hand, generating the economic benefits associated with unfettered data flows across borders and, on the other hand, providing a trusting environment for individuals, firms and governments taking part in the data-driven economy. International trade agreements seek to regulate data flows through provisions aiming to facilitate the cross-border trade of goods and services built on data, such as data processing and other computing services.Footnote 1
On the margins of the G20 leaders’ meeting in Osaka in June 2019, twenty-three countries plus the European Union (EU) signed the Osaka Declaration on the Digital Economy.Footnote 2 The declaration states that the signatories, ‘standing together with other World Trade Organization (WTO) Members that participate in the Joint Statement on Electronic Commerce issued in Davos on 25 January 2019, in which 78 WTO Members are on board, hereby declare the launch of the “Osaka Track”, a process which demonstrates our commitment to promote international policy discussions’. The referred-to January 2019 Joint Statement, issued during the World Economic Forum’s annual meeting in Davos, confirms the members’ ‘intention to commence WTO negotiations on trade-related aspects of electronic commerce’.Footnote 3 This Joint Statement is itself a restatement of a previous Joint Statement issued at the WTO’s eleventh ministerial conference in Buenos Aires in December 2017, where some seventy-five members ‘recognize[d] the important role of the WTO in promoting open, transparent, non-discriminatory and predictable regulatory environments in facilitating electronic commerce’.Footnote 4 The Buenos Aires Joint Statement indicated that the signatories would begin exploratory work toward ‘future WTO negotiations on trade-related aspects of electronic commerce’.Footnote 5
A number of discussion rounds took place in 2018 and 2019 in Geneva in order to delimit the scope of potential plurilateral negotiations on electronic commerce/digital trade. The provisions on e-commerce/digital trade found in the Comprehensive and Progressive Agreement for Trans-Pacific Partnership (CPTPP)Footnote 6 and the United States–Mexico–Canada Agreement (USMCA),Footnote 7 the North American Free Trade Agreement’s (NAFTA) replacement, are currently the most detailed proposals being considered in the WTO’s plurilateral negotiations on e-commerce.Footnote 8
This is why this chapter offers a detailed analysis of these CPTPP/USMCA e-commerce/digital trade provisions that pertain to data flows in order to identify the constraints they could impose on national data regulation.Footnote 9 To do so, it uses Canada as an example, because it is a party to both trade agreements and it seeks to build a high-trust data environment for consumers and businesses.Footnote 10 The analysis leads to the conclusion that Canada’s CPTPP and USMCA commitments could ultimately negate the effectiveness of future data protection policies that the Canadian federal government might want to adopt to achieve its ‘trust in the digital age’ objective.Footnote 11
B Cross-Border Data Flow and National Data Regulation
Policymakers have lots of reasons to try to link the free flow of data and data protection. According to Dan Ciuriak, ‘there is a need for free flow of data, including on a cross-border basis’, because data is ‘intrinsic to commercial transactions’.Footnote 12 He sees data as the ‘fifth freedom’ of commerce, with free movement of goods, services, capital and labour as the other four. Legal and regulatory limits on cross-border data flows can, however, act as beyond-the-border obstacles to trade.Footnote 13 For instance, Martina Ferracane and Erik van der Marel find that policies that restrict the cross-border flow of data have a negative impact on trade in digital services.Footnote 14
In certain circumstances (for example, to protect privacy, security, competition, culture, and so on), there is a need for the regulation of data collection, access, use and transfer. For example, the use of and access to people’s data should be fair, transparent, accountable and subject to individuals’ explicit consent. Moreover, the use of personal data should not lead to discrimination and bias when people seek to obtain a good or a service, whether it is from the private or the public sector. Another example is the protection of proprietary business data against uncompensated commercialization by others. On the other hand, access to data should not be controlled in such a way that it limits competition and innovation.
So the big question for policy-makers is how to allow for data to flow freely across borders while maintaining a high degree of trust among individuals, firms and governments that they will not be harmed in terms of privacy, consumption (price, choice or access), competition, innovation, security and so on. Strong data protection laws and regulations are necessary to create such trust. The problem is that such laws and regulations, if developed independently from other countries, can limit the cross-border flow of data and have negative economic consequences. This is the balancing act that the countries taking part in the WTO’s plurilateral negotiations on ‘trade-related aspects of electronic commerce’ are trying to achieve.
C The CPTPP, the USMCA and National Data Regulation: Example from Canada
This section analyzes the electronic commerce/digital trade chapters included in the CPTPP and the USMCA in order to determine how they may affect data regulation in Canada, in order to provide an example of the potential impact that a WTO plurilateral agreement on trade-related aspects of electronic commerce modeled on CPTPP/USMCA provisions could have on members’ governments’ ability to regulate data nationally. Since the CPTPP’s electronic commerce chapter provided the basis for the USMCA’s digital trade chapter, the analysis focuses first on the CPTPP.Footnote 15
I The CPTPP
The CPTPP contains several provisions in its chapter 14 (electronic commerce) that concern data flows.Footnote 16 Chapter 14 does not specify what types of data are covered, except to say those that are necessary for business purposes. It also preserves member states’ ability to limit the free flow of data held by government entities and encourages interoperability between data privacy regimes as well as cooperation between consumer protection authorities.
Here are the CPTPP’s main provisions relating to data flows:
Consistent with the WTO’s waiver on customs duties on electronic commerce, Article 14.3 prohibits the imposition of customs duties on electronic transmissions; however, it allows ‘internal taxes, fees or other charges’ as long as they are not discriminatory (i.e., applied equally to national as well as foreign entities).Footnote 17 As such, the CPTPP does not discriminate among various types or sources of data.
Article 14.8 CPTPP mandates a personal data protection floor: it ensures that parties have laws and regulations that provide a minimum level of personal information protection but it is flexible as it accommodates different national approaches.Footnote 18
Article 14.11 protects the free flow of cross-border data for business purposes,Footnote 19 although it allows restrictions on such flows in order to achieve a ‘legitimate public policy objective’.Footnote 20
Article 14.13 prohibits the obligation for a business to locate specific computing facilities in exchange for market access.Footnote 21 In other words, it prohibits parties from imposing data localization requirements. However, the ‘legitimate public policy objective’ exception also applies in this case.
Article 14.17 prohibits requirements that source code be transferred or accessed as a condition of import.Footnote 22 The prohibition is, however, limited to mass-market software but not when it is used in critical infrastructure.Footnote 23 The prohibition also does not apply to requests for source code modification to comply with domestic laws of regulations, as long as the latter are not inconsistent with the CPTPP; that is, they are not discriminatory in nature and apply equally to domestic and foreign firm.Footnote 24
Article 14.2(3) CPTPP stipulates that ‘this Chapter shall not apply to: (a) government procurement; or (b) information held or processed by or on behalf of a Party, or measures related to such information, including measures related to its collection’. This means that prohibitions on data transfer restrictions and data localization found in Articles 14.11 and 14.13 do not apply to governments. Therefore, the requirements imposed by the federal and some provincial governments that personal information held by public bodies be kept and processed in Canada are exempted under the CPTPP. This exception is potentially important if Canadian governments wish to make more publicly collected data available for analysis (for example, for artificial intelligence [AI] training purposes) but want to ensure that they retain control over them to protect individuals, as well as the state.
The scope of application of Article 14.2(3) CPTPP is, however, somewhat ambiguous, when it comes to subnational governments, especially part (b). This is because Article 1.3 defines ‘Party’ as ‘any State or separate customs territory for which this Agreement is in force’. As such, it would exclude subnational governments at the provincial and municipal levels, especially since ‘regional level of government’ is defined separately in Article 1.3.Footnote 25 The term ‘government procurement’ in part (a) is less ambiguous. Article 15.2(2) CPTPP establishes the scope of application of government procurement: ‘For the purposes of this Chapter, covered procurement means government procurement: (a) of a good, service or any combination thereof as specified in each Party’s Schedule to Annex 15-A’. In Canada’s schedule in Annex 15-A, section B deals with sub-central government entities.Footnote 26 Government procurement provisions do not apply to schools, universities, hospitals and Crown corporations for all provinces and territories except Ontario and Quebec.Footnote 27 This means that only in Ontario and Quebec (the excluded provinces) could such public entities impose localization restrictions with respect to data storage and processing in their procurement contract
Articles 14.11 and 14.13 CPTPP on the prohibition of, respectively, restrictions on cross-border data transfers for business purposes and requirements to localize the storage of data domestically, both contain an exception for a ‘legitimate public policy objective’. This means that CPTPP parties, such as Canada, can restrict the in-and-out flow of data in order to pursue such an objective. The big question, however, is: what is a ‘legitimate’ objective? Article 14.11(3) states that a measure restricting cross-border data transfers cannot: (i) be ‘applied in a manner which would constitute a means of arbitrary or unjustifiable discrimination or a disguised restriction on trade’ and (ii) ‘impose restrictions on transfers of information greater than are required to achieve the objective’. Article 14.13(3) offers the same limitation on the ‘legitimate public policy objective’ (also called general) exception:
Nothing in this Article shall prevent a Party from adopting or maintaining measures inconsistent with paragraph 2 to achieve a legitimate public policy objective, provided that the measure: (a) is not applied in a manner which would constitute a means of arbitrary or unjustifiable discrimination or a disguised restriction on trade; and (b) does not impose restrictions on the use or location of computing facilities greater than are required to achieve the objective.
Michael Geist questions whether privacy protection would qualify under the above-mentioned exception.Footnote 28 He seems doubtful when he writes: ‘the [CPTPP] restriction on the use of data localization requirements may pose an insurmountable barrier’.Footnote 29 The same conclusion would apply to Article 14.11 CPTPP on data transfers. For instance, in early April 2019, the Office of the Privacy Commissioner of Canada (OPC) released a consultation paper on transborder data flows in which it indicates that it would require a company to obtain prior consent from individuals before moving their personal data outside of Canada.Footnote 30 According to Geist, this new approach ‘is a significant reversal of longstanding policy that relied upon the accountability principle to ensure that organizations transferring personal information to third parties are ultimately responsible for safeguarding that information’.Footnote 31 The OPC stated that this new approach would be consistent with Canada’s international trade obligations but Geist is not so sure: ‘The imposition of consent requirements for cross-border data transfers could be regarded as imposing restrictions greater than required to achieve the objective of privacy protection, given that PIPEDA [Personal Information Protection and Electronic Documents Act] has long been said to provide such protections through accountability without the need for this additional consent regime’.Footnote 32
Andrew Mitchell and Neha Mishra, for their part, also point out that there is the potential for conflict between e-commerce or digital trade chapters in free trade agreements (FTAs) and WTO agreements, such as the General Agreement on Trade in Services (GATS).Footnote 33 They write that Article XIV GATS provides the basis for the general exception found in FTA provisions, such as the CPTPP’s Articles 14.11 and 14.13; however, they also note that ‘these exceptions may be unable to address all aspects of data flow restrictions’.Footnote 34 In addition, Mitchell and Mishra mention that ‘strict scrutiny of these measures [restricting data flows] under international trade law may lead to unsatisfactory outcomes because GATS Articles XIV and XIV bis are limited in scope and do not facilitate consideration of Internet trust issues holistically’.Footnote 35 The above implies that general exceptions on data transfers and data localization found in the CPTPP may not offer as much policy flexibility as originally thought with respect to future laws and regulations that Canadian (federal and provincial) governments might want to put into place to govern data in order to ensure trust as well as stimulate innovation.
Given that algorithms ‘drive what news content and advertising each of us sees online [and] will be used by governments to decide who receives or is denied benefits’,Footnote 36 it is reassuring that Article 14.17 CPTPP does not prevent governments from regulating and supervising source codes, as long as it is not done in a protectionist way against foreign producers. Teresa Scassa notes that it is necessary to be able to access the source code of an app, software or AI in order to evaluate algorithms’ performance and potential biases.Footnote 37 Such enquiries are important if governments want to protect consumers, workers and businesses from suffering the negative consequences associated with, for example, fraud or discrimination.
II The USMCA
The USMCA, unlike NAFTA, which it replaces, contains a chapter (19) on ‘digital trade’ (not ‘e-commerce’, in order to signify its broader scope) that builds on the CPTPP’s chapter 14.Footnote 38 As such, the USMCA introduces a number of differences from the CPTPP. The following analysis focuses on these differences.
One significant difference with the CPTPP concerns the requirement for USMCA member states to ‘adopt or maintain a legal framework that provides for the protection of the personal information of the users of digital trade’.Footnote 39 While the USMCA does not prescribe specific rules or measures that a party must take to protect privacy, it goes further than the CPTPP by providing more guidance to inform a country’s privacy regime. In particular, the USMCA refers explicitly to the APEC (Asia-Pacific Economic Cooperation) Privacy Framework and OECD (Organisation for Economic Co-operation and Development) Guidelines as relevant ‘principles and guidelines’ when developing a legal framework for protecting personal information.Footnote 40 Unlike the CPTPP, the USMCA also mentions key principles that parties should follow as they develop their legal framework.Footnote 41
In addition, the USMCA stipulates that the parties ‘recognize the importance of … ensuring that any restrictions on cross-border flows of personal information are necessary and proportionate to the risks presented’,Footnote 42 thereby providing some limit on the extent to which data protection legislation or regulation can constrain cross-border personal data flows. Such a standard for potentially restricting data flows in order to protect personal information is not present in the CPTPP’s Article 14.8(2). As such, the USMCA provides some guidance, albeit vague, to future panel arbitrators in interpreting the ‘legitimate public policy objective’ exception in the case of a dispute involving limits imposed on cross-border data flows by one of the USMCA parties. The big issue in this case is what ‘necessary and proportionate’ mean in the context of protecting personal information? For instance, would a requirement for organizations in Canada to obtain explicit consent from individuals before the latter’s data are transferred across the border to the United States be deemed necessary and proportionate?
What is probably the most important difference between the USMCA and the CPTPP is the former’s Article 19.17 on Interactive Computer Services, which has no equivalent in the CPTPP. According to this article, Internet service providers, social media platforms and search engines cannot be treated as information content providers for liability purposes, which means ‘immunity from legal consequences for content generated by users’.Footnote 43 However, Annex 19-A(4) states: ‘For greater certainty, Article 19.17 (Interactive Computer Services) is subject to Article 32.1 (General Exceptions), which, among other things, provides that, for purposes of chapter 19, the exception for measures necessary to protect public morals pursuant to paragraph (a) of Article XIV of the GATS is incorporated into and made part of this Agreement, mutatis mutandis’. This paragraph opens the door for potential limits on the article’s scope and application but, as mentioned earlier, there is a lot of uncertainty with respect to the general exception’s reach.Footnote 44 In any case, the USMCA’s Article 19.17 will likely make it harder for Canadian governments to develop measures to protect individuals and consumers of social media, search engines and other user-generated content providers from the consequences of disinformation (for example, ‘fake news’).
Another noteworthy difference between the USMCA and the CPTPP concerns source code and algorithms. First, the USMCA’s Article 19.16 gets rid of the CPTPP’s Article 14.17(2).Footnote 45 This implies that all types of source code are covered by the USMCA, without exception. As Scassa notes: ‘This may raise some interesting concerns given the growing government use of software and algorithms in key systems and processes’.Footnote 46 The USMCA also does not contain the CPTPP’s provision on allowing requests for source code modification.Footnote 47 Instead, it offers Article 19.16(2), which does not exist in the CPTPP: ‘This Article does not preclude a regulatory body or judicial authority of a Party from requiring a person of another Party to preserve and make available the source code of software, or an algorithm expressed in that source code, to the regulatory body for a specific investigation, inspection, examination, enforcement action, or judicial proceeding, subject to safeguards against unauthorized disclosure’. Scassa says that the difference between the USMCA and the CPTPP provisions is ‘important given that we are already facing context in which it is necessary to understand the algorithms that lead to certain decisions [for example, litigation involving autonomous vehicles]’.Footnote 48 So the USMCA improves on the CPTPP in terms of source code transparency but it is also a step back when it comes to the absence of a provision allowing requests to modify algorithms, which could be found to be biased or causing harm to people, businesses or governments. With the USMCA, unlike the CPTPP, a Canadian request for algorithmic modification could be challenged as a protectionist measure discriminating against the US or Mexican producer of the software or application.
The final difference between the USMCA and the CPTPP is with respect to the provisions on data localization (‘Location of Computing Facilities’). In the CPTPP’s Article 14.13, ‘the Parties recognise that each Party may have its own regulatory requirements regarding the use of computing facilities, including requirements that seek to ensure the security and confidentiality of communications’Footnote 49 but ‘no Party shall require a covered person to use or locate computing facilities in that Party’s territory as a condition for conducting business in that territory’Footnote 50 unless it is for a ‘legitimate public policy objective’.Footnote 51 For its part, the USMCA’s Article 19.12 only has one provision: ‘No Party shall require a covered person to use or locate computing facilities in that Party’s territory as a condition for conducting business in that territory.’ This means that, unlike the CPTPP, the USMCA does not allow its parties to invoke a ‘legitimate public policy objective’ exception to impose a data localization requirement to firms from the other two parties as a condition for providing a digital good or service in the territory. The only exception possible here is for the specific case when a digital good or service is provided to a government, because the USMCA’s chapter 19 does not apply to ‘government procurement; or except for Article 19.18 (Open Government Data), to information held or processed by or on behalf of a Party, or measures related to that information, including measures related to its collection’.Footnote 52 Therefore, governments can only require organizations that collect, hold or process information to locate their computing facilities in the territory when these activities are undertaken for or on behalf of a government, which is in line with current practices. However, if, for example, data deemed critical for national security reasons were held by a private organization, then the USMCA would technically require a government to allow these data to be held and processed in the other two member states’ territory. As a result, these data could become accessible to the other member state governments (for example, through the USA PATRIOT Act in the United States).
III Interim Conclusion
With the CPTPP and the USMCA, Canada has adopted obligations that provide for the free flow across borders of data for business purposes while, in principle, protecting consumers, personal information and government-related data. However, as analyzed earlier, these two trade agreements also pose potential obstacles to Canada’s ability to effectively regulate data and it is unclear how much policy flexibility they leave to the federal and provincial governments to pursue legitimate objectives and protect the vital interests of their citizens. It will ultimately be left to state-to-state dispute settlement panels in the CPTPP and the USMCA (as well as the investor–state dispute settlement mechanism in the CPTPP) to resolve this uncertainty and determine the scope of Canada’s national data regulation. If dispute settlement panels were to rule in favour of cross-border data flows and impose limits on Canada’s ability to ensure trust among individuals and businesses when it comes to the data-driven economy, then such decisions could undermine the CPTPP’s and the USMCA’s legitimacy and political support.
D Key Proposals at the WTO’s Plurilateral Negotiations on Trade-Related Aspects of Electronic Commerce
In April 2019, the key players in the negotiations – China, the EU and the United States – issued their proposals to the WTO’s plurilateral negotiations on trade-related aspects of electronic commerce.Footnote 53 The Chinese proposal is the least ambitious. It is hortatory in nature and focuses on principles for the facilitation of cross-border electronic commerce, leaving aside data flows.Footnote 54 China’s proposal is thus in line with the electronic commerce provisions contained in some of the FTAs that it has signed so far. As such, it reflects the country’s desire to protect its walled-off digital realm.Footnote 55
The EU’s proposal goes much further than the Chinese one. For instance, it offers specific provisions that mandate unrestricted cross-border data flows,Footnote 56 subject to national rules deemed ‘appropriate to ensure the protection of personal data and privacy’.Footnote 57 The EU’s proposal also stipulates that there can be no requirement for the transfer of software source codes in exchange for market access, although it can be required for legal violations or national security reasons.Footnote 58
The US proposal, for its part, follows closely the digital trade chapter found in the USMCA.Footnote 59 As such, it supports the EU’s position on cross-border data flows, personal data protection and source codes; however, unlike the EU’s proposal, which states that ‘[n]othing in the agreed disciplines and commitments shall affect the protection of personal data and privacy afforded by the Members’ respective safeguards’,Footnote 60 the US offer qualifies the limits on cross-border data flows that national data protection regimes can impose: ‘ensuring that any restrictions on cross-border flows of personal information are necessary and proportionate to the risks presented’ (Article 7.4), which follows USMCA’s Article 19.8.3. Article 8 of the US proposal also restates, verbatim, the USMCA’s provisionFootnote 61 that only restrictions on cross-border data flows that ‘achieve a legitimate public policy objective’ are acceptable. Finally, the USMCA’s Article 19.17 (‘Interactive Computer Services’) is transposed in its entirety into the US proposal,Footnote 62 thereby putting forward the prohibition on treating ‘a supplier or user of an interactive computer services as an information content provider in determining liability for harms related to information stored, processed, transmitted, distributed, or made available by the service, except to the extent that the supplier or user has, in whole or in part, created or developed the information’.Footnote 63
In sum, the proposals occupy different places on a continuum that includes independent national data protection at one end and cross-border data free flow at the other, with China being close to the former pole while the United States is closer to the other pole and the EU is somewhere in between (see Figure 14.1). As analyzed earlier, the USMCA’s digital trade chapter, which itself builds on the CPTPP’s chapter 14, has served to inform the US position in the WTO’s Plurilateral ‘Trade-related Aspects of Electronic Commerce’ negotiations. Should the latter ever prevail, which remains to be seen in light of the divergent key positions on offer, it will make it difficult for member states to adopt national data regulations that impose limits on the cross-border flow of data, most especially personal data.
E Conclusion and Outlook
As the example of Canada demonstrates herein, the CPTPP and the USMCA require their members to adopt obligations that provide for the free flow across borders of data for business purposes while, in principle, protecting consumers, personal information and government-related data. However, as analyzed above, these two trade agreements also pose potential obstacles to a member state’s ability to effectively regulate data and provide a trustworthy environment for individuals, businesses and governments. The analysis shows that it is not at all clear how much policy flexibility the CPTPP and the USMCA ultimately allow governments that want to adopt new laws and regulations to, among various objectives, protect people’s privacy, prevent algorithmic bias, protect critical infrastructure, ensure national security or promote domestic innovation.
For the plurilateral negotiations of an agreement on ‘trade-related aspects of electronic commerce’ at the WTO, this means that the US proposal, which is closely derived from the USMCA’s digital trade chapter,Footnote 64 would create a lot of uncertainty as to how much limits on cross-border data flows a country could impose via its national data regulation regime, until dispute-settlement panels decide on the acceptability and legitimacy of national data rules in restricting data flows across borders.
To leave such crucial decisions for economy and society in the hands of unelected and unaccountable individuals seems an odd way to govern the data-driven economy’s future functioning. A better approach would be to remove issues related to data regulation and standards from the WTO negotiations and push for a separate international regime to govern data and its cross-border flows.Footnote 65 Just like capital (or financial) flows are not part of the WTO’s framework,Footnote 66 which limits itself to rules on trade in financial services, so should data flows be excluded from an eventual agreement on trade-related aspects of electronic commerce. The latter agreement, should it ever see the light of day, should instead focus its attention solely on the rules governing trade in digital goods and services. A separate international body (such as an International Data Standards Board) should be responsible for setting standards that regulate the creation, processing, use, distribution and transfer of data, both personal and non-personal. All countries that apply and enforce these standards would be allowed to take part in a single data area where data would be free to flow across member states’ borders. The WTO’s rules on digital trade would be left to deal with possible infringement of core trade principles, such as non-discrimination.
A Introduction
The digitalization and the increase in global trade significantly impact the economy and citizens of Europe. European policymakers are well aware of these developments and wish to unlock the potential of the digital economy through the EU’s Digital Single Market Strategy.Footnote 1 One core goal of this strategy, promoted by the European Commission since 2015, is the pursuit of a free flow of data within the EU. Such a free flow should encourage the creation of and access to goods and services that – in their essence – collect and process vast amounts of data.
While the free flow of data is desirable from an economic perspective, as it maximizes the use of data by businesses throughout (and beyond) the EU, an entirely free flow of personal data goes against individuals’ interests to exercise some control over the collection and use of their data by third parties. Therefore, a balance between economic and individual interests must be struck by creating a regime that ensures both. We call this desired balance an ‘adequate free flow of data’. The term ‘adequate’ implies that a European digital economy should achieve more than economic welfare and simultaneously protect the interests of European citizens and consumers, especially their fundamental rights, such as the right to personal data protection. The balancing of interests could also benefit the digital economy, as it would promote the European citizens’ trust and confidence in the digital single market in order to enable the full exploitation of its potential. To achieve trust and confidence, legitimate boundaries to the free flow of data must be set.
Policymakers in the EU have debated whether the digital economy may benefit from the introduction of data ownershipFootnote 2 and data access rights,Footnote 3 and legal scholars have analysed how such rights could lead to a digital economy benefitting all stakeholders. Yet policymakers and scholars have sometimes had different understandings of the term ‘ownership’, most often inadvertently. First, data ownership can be understood as a property right derived from civil law concepts of property in real estate and chattel, or intellectual property rights. This understanding of ‘ownership’ is how lawyers usually conceive the term. Second, data ownership can also be understood more broadly as a right that grants some control over data. It is this sort of ownership that non-lawyers typically have in mind when they advocate for the introduction of a ‘data ownership right’, most often (and again inadvertently) having only personal data in mind. With regard to personal data, this second understanding aligns with the approach taken in data protection law, namely in the EU’s General Data Protection Regulation (GDPR),Footnote 4 which grants data subjects some control over their personal data. In contrast to data ownership, data access rights serve a different purpose – to empower individuals and businesses to obtain access to data that is of specific interest to them. Individuals have a legitimate interest in having access to personal data which is processed by businesses; the same is true for non-personal data that individuals have stored with a third party, such as a cloud provider. For businesses, access to data may be of key importance when offering innovative goods and services in the digital economy, as the use of specific data may be necessary to enter a new market or to remain competitive in an existing one.
In this chapter, we refrain from recapitulating the thorough academic debate on data ownership and data access rights.Footnote 5 Instead – and considering this book’s broader perspective of big data and global trade – we look at the topic from a different angle and ask whether and how the concepts of data ownership and data access rights may serve the goal of establishing an adequate free flow of data in the digital single market.
In the pursuit of the chapter’s objective, we first map the policy goals contained within the EU’s Digital Single Market Strategy. Upon this basis, we analyse how data ownership – understood as a property right – may serve the implementation of this strategy. Based on the insight that introducing property rights in data is unlikely to help implementing an adequate free flow of data, we examine in the following section of the chapter whether ownership as control over personal data is a viable alternative to the property rights approach. As a final step, we examine if, and under what circumstances, access rights to data already exist, or should be introduced, to allow individuals and businesses to use both personal and non-personal data. The last part concludes and explores paths towards strengthening data access rights, for instance, through the introduction of a compulsory licences regime.
B The Digital Single Market Strategy: Basic Features and Objectives
In a nutshell, the goal of the EU Digital Market Strategy is to ensure that individuals and businesses have access to online services and products and that the requirements of fair competition, consumer and data protection as well as copyright are being fulfilled. In addition, no geo-blocking should occur within the Union.Footnote 6 In line with the general objective of fostering the internal market, the Digital Single Market Strategy aims to ‘tear down the regulatory walls and move from 28 national markets to a single one’,Footnote 7 while maintaining confidence in the digital economy. In order to promote the availability of good quality and interoperable datasets, EU policymakers seek to abolish inappropriate restrictions to the free flow of data across member states. Additionally, the European Commission wants to facilitate the value generation from datasets by training their citizens in the respective fields, by cooperating with industry and universities to determine the adequate skills required for the labour market and by promoting access to and transfer of knowledge amongst the private and the public sector.Footnote 8
These statements show that the free flow of data is a key policy goal to enable the EU to compete in the global digital economy. But limitations are necessary to create a balanced approach that takes into account the needs of businesses and individuals alike. Some of the latter fear an ever-increasing collection and unrestricted processing of their personal data. In light of the power and information asymmetries between data processing entities and individuals, this fear is understandable and well-founded, as individuals are left with little or no control over how their personal data is being processed.Footnote 9 Thus, an important distinction needs to be made between the free flow of personal and non-personal data.
While some individuals fear a lack of control over their personal data, they hardly care about the collection and use of non-personal data. Accordingly, Europeans seem to be quite comfortable with the free flow of non-personal data.Footnote 10 In contrast, when it comes to personal data, an arguably central foundation of the digital single market is the establishment of a ‘strong, consistent and comprehensive data protection framework for the EU’.Footnote 11 For users to have sufficient trust and confidence in the free flow of personal data, rules governing this flow must be adopted, and the European Commission sees the GDPR as the critical building block to do so. According to the commission, the GDPR is the central piece of legislation for the development of ‘innovative and sustainable data goods and services’,Footnote 12 and ‘the foundation for the free flow of personal data in the EU’, as it ‘bans prohibitions and restrictions to the free movement of personal data for reasons connected with the protection of natural persons with regard to the processing of personal data’.Footnote 13 Even if restrictions to the free flow can be justified by other reasons (e.g. under taxation and accounting laws), the GDPR is seen as an important step to abolish data localisation restrictions – i.e., rules mandating local storage or processing activities. In fact, as data localization requirements of member states are a major obstacle to the free flow of data,Footnote 14 the abolishment of such restrictions is key to promote a flourishing European data economy.Footnote 15
Yet, while the GDPR certainly fosters a free flow of personal data within the EU by establishing a (relativelyFootnote 16) uniform regime in all EU member states, it also imposes substantial restrictions on the processing of personal data and thereby limits the free development and deployment of digital goods and services. While innovation remains possible, the GDPR has at least raised its costs, sometimes to a level making the deployment of innovative digital goods and services economically unfeasible.Footnote 17 These restrictions, however, are taken into account with the aim of protecting European citizens from the risks associated with the processing of their personal data. The tension between the free movement of personal data within the EU and the protection of the fundamental rights and freedoms of individuals is prominently highlighted in Article 1 GDPR, which addresses both goals in a separate paragraph. Interestingly, the European legislator is quite clear on the priority of the two objectives by stating that ‘[t]he free movement of personal data within the Union shall neither be restricted nor prohibited for reasons connected with the protection of natural persons with regard to the processing of personal data’ (Article 1(3) GDPR). While it is doubtful whether this priority of objectives is actually put into action by the provisions of the GDPR, this statement supports our perspective that any (potential) regulation on personal and non-personal data should be analysed with regards to its ability to ensure an adequate free flow of data.
C Data Ownership
I Ownership as a Property Right
1 State of Research
The literature on data ownership as a property right is divided: While some authors argue that the current regulatory system is inadequate to protect individuals in the digital economy, others consider it adequate (or adequate enough) and therefore do not encourage the establishment of property rights in data. A first group of authors highlights the potential threats of big data and global trade for the protection of the fundamental rights and freedoms of European citizens. Data ownership, they argue, could help cushion some of the adverse effects of the digital economy.Footnote 18 The idea behind their string of reasoning is that, by assigning data to the person to whom it refers, the individual data ‘owners’ are put in a better negotiating position towards companies and thus a fairer distribution of the value created by the data processing can be ensured.Footnote 19 One strong proponent of a data ownership right even argues that such a right would empower individuals to combat the ‘totalitarian digital appropriation strategies’ of big tech companies.Footnote 20 Yet even proponents of data ownership as a property right acknowledge that the practical implementation of such a right remains unclear.Footnote 21 In fact, so far, only abstract calls for data ownership frameworks have been proposed.Footnote 22
A second group of authors starts from the assumption that data is a public good.Footnote 23 This means that the use of data is non-rivalrous, as data can be used by an unlimited number of individuals simultaneously, and the use of one individual does not interfere with the use of others. Against this background, introducing data ownership needs a convincing justification as such a property right would allow data owners to exclude others from using their data. According to these authors, property rights in public goods should only be granted in case of market failure, i.e. if data was not produced or used to a socially desirable degree.Footnote 24 However, in the age of big data one can hardly argue that a market failure with respect to the collection, creation, and processing of data exists. To the contrary, the exponential rise of the quantity and quality of data and its ubiquitous processing indicates that companies have enough incentives for collecting, processing, and trading data.Footnote 25 Even if incentives for the collection, processing, and trading of data exist, these activities might not lead to socially desirable outcomes. Nonetheless, it is doubtful whether these outcomes amount to an actual market failure and even more doubtful that such failure could be remedied by the introduction of propert rights in data.
A third group of authors excludes the introduction of data ownership rights from a fundamental rights perspective. They argue that the fundamental right to the protection of personal data safeguards the personality of data subjects, not their property.Footnote 26 Accordingly, a data subject cannot be ‘regarded only or mainly as the owner of the data concerning him or her’,Footnote 27 as such ownership would allow data subjects to trade their property rights away and thereby waive the guarantees of their fundamental rights.Footnote 28 From this perspective, granting property rights in personal data is impossible, as individuals are not free to waive or completely alienate the rights in their personal data. According to these authors, only some rights in their data could be transferred from data subjects to third parties, but not all of them.Footnote 29 For instance, a waiver of all data protection guarantees would not be permissible, but a numerus clausus of clearly defined ‘leases’ of personal data for specific purposes could be set in place.Footnote 30
With regard to the question whether the introduction of data ownership as a property right would foster an adequate free flow of data in the digital single market, other aspects are of crucial importance, namely the impact of such property rights on transaction costs and (as a result) on the use of data and the consequences for data subjects. We look in turn at these implications.
2 Analysis
a Transaction Costs
The introduction of property rights in data would lead to a situation in which every transfer and use of data would have to be subject to a prior agreement with the owner of the data. First of all, the owner of the data to be used would have to be identified. Second, the potential user would have to negotiate with the owner and agree on whether and under what conditions the data can be used. Both the identification of the owner and the negotiation would lead to considerable transaction costs.Footnote 31
Identifying the data owner might sometimes be straightforward but will more often be rather complicated. The former would be true for non-personal data which is controlled by a single entity, most often a business. The latter would apply to personal data. If one assumes that property rights in personal data would vest in data subjects, the use of large datasets containing data about a large number of individuals would quickly become very burdensome, as every data subject would have to be identified and contacted in order to negotiate the conditions for the use of their data. Although there are important differences between the transaction costs associated with the use of personal and non-personal data, the introduction of data ownership as a property right would increase transaction costs in all cases and thus hurt the free flow of data within the digital single market. With regard to personal data, one might argue that these transaction costs must be incurred to protect the interests of data subjects in having control over the use of their personal data, thus moving from a fully free flow to a somewhat restricted and more adequate free flow of personal data. Increasing transaction costs for using and trading non-personal data by introducing data ownership rights and thereby restricting the free flow of data cannot be justified.Footnote 32
Some scholars have argued that property rights in data could (in theory) increase legal certainty and reduce transaction costs, as contract negotiations could start from a clear determination as to who owns what data.Footnote 33 However, an analysis of potential criteria for allocating property rights in data shows that it is far from obvious which criteria should be applied to determine ownership, especially with regard to non-personal data.Footnote 34 While it seems intuitive that data subjects should be the owner of personal data relating to them, it is less clear if businesses collecting such data should likewise have some ownership over the data accumulated in their systems. Besides, personal data quite often relates to more than one individual; for instance, a picture of a group of people or the genetic data of one person which always of data about that person’s parents, grandparents, siblings, infants, etc. Concerning the difficulties of identifying and applying a suitable criterion for allocating property rights in data, introducing data ownership rights would rather raise than reduce transaction costs and limit the free flow of data in the digital single market.
b Consequences for Data Subjects
The introduction of property rights in personal data would most probably have negative consequences for data subjects. Even if data controllers most often process personal data based on legitimate interests (Article 6(1)(b), (c) and (f) GDPR),Footnote 35 another important foundation for the lawfulness of processing is the data subjects’ consent (Article 6(1)(a) GDPR). If the processing is based on consent, data subjects can – at least in theory – decide whether businesses may use their personal data by accepting their terms and conditions and/or their privacy policies. In doing so, they ‘trade’ their personal data in exchange for ‘free' goods and services. However, under the current data protection regime, consent can be withdrawn by data subjects at any time (Article 7(3) GDPR), thereby enabling them to prohibit the future processing of their personal data, if they reconsider their previous decision.
Granting property rights in personal data would mean that these property rights could be transferred to third parties.Footnote 36 Given this possibility, we have to expect that businesses would request that users of their services transfer those property rights to them – just as they currently request users to allow for an all-encompassing use of their data through consent. As opposed to the situation today, however, businesses that acquire their users’ property rights in their personal data would be able to exclude these users from using their personal data themselves and from exercising the limited amount of control they have today. As a result, introducing property rights in personal data would substantially weaken the position of data subjects – which is the contrary of what people advocating for such rights want to achieve. While the option to transfer ownership rights in personal data might have a positive impact on the free flow of such data, the interests of data subjects in being able to exercise some control over the processing of their personal data would be neglected. As a consequence, the introduction of property rights in personal data would compromise the goal of establishing an adequate free flow of data.
3 Interim Conclusion
The analysis shows that introducing data ownership as a property right does not promote the goals of the Digital Single Market Strategy. For non-personal data, granting property rights would raise transaction costs and thereby deter or at least encumber its free flow. Accordingly, legislators should not introduce any property right in such data. Moreover, there are no reasons why the free flow of non-personal data should be restricted by any other legal means. On the contrary, the full potential of non-personal data can be achieved if that data is shared amongst businesses, for instance, through the granting of access rights, as discussed later.
While property rights in personal data would also increase transaction costs, these costs could be justified with regard to the goal of protecting the interests of data subjects in having some control over the use of their personal data. However, the granting of property rights in personal data would lead to a different and quite severe problem: Since property rights in personal data could be transferred to any third party, businesses would most likely make sure that their users transfer these property rights when using their services. Consequently, data subjects would not only lose control over their personal data but businesses, as the owners of said data, could even forbid them to further use their personal data altogether. Such a scenario would undermine the policy goal of establishing an adequate free flow of personal data within the EU.
II Ownership as Control
1 Preliminary Remarks
The concept of ‘ownership as control’ is generally accepted and well-established for personal data and is usually called ‘informational self-determination’ or ‘informational autonomy’.Footnote 37 These notions refer to the individual’s right to determine which information about them is disclosed to others and for what purposes such information will be used.Footnote 38 Data protection laws are generally based on these concepts. The GDPR is even quite explicit about this underlying rationale by stating that ‘natural persons should have control of their own personal data’ (Recital 7). The concept of control is most clearly expressed in the condition of consent for the lawfulness of data processing (Article 6(1)(a) GDPR) and in the individual rights of the data subjects (Articles 12 et seqq. GDPR). In the following sections, these concepts are analysed further to assess whether ownership as control is a meaningful approach to establish an adequate free flow of personal data.
2 Implementation
a Consent
At the stage of collection, consent and the right to information are the fundamental principles within the GDPR for granting control. In order to be compliant with the GDPR, consent must represent a ‘freely given, specific, informed and unambiguous indication’ by the data subjects by which they state or clearly affirm their agreement with the processing of personal data relating to them (Article 4(11) GDPR). It is key that the data subjects have a real choice to agree or disagree to the data collection. Such a choice is challenged in cases of power imbalances or if consent is the condition for the performance of a contract or for the provision of a service (Article 7(4) GDPR).Footnote 39 Similarly, any form of deception, intimidation, or significant negative consequences for the data subjects if they do not consent or later withdraw consent will fail to fulfil the requirement of a freely given consent.Footnote 40
Consent is given on an informed basis if the data subjects are able to understand who processes what data for which purpose(s), if they are made aware of their right to withdraw consent, and if they obtain information about the use of their data for automated decision-making, as well as on the risk associated with a transfer of the data to an unsafe third country.Footnote 41 More often than not, the necessary information is provided in the controllers’ privacy policy or as a specific part of the general terms of service. In either case, the information must be provided in an intelligible and accessible form, using clear and plain language (Article 7(2) GDPR).
Due to the complexity of digital goods and services, being adequately informed about the data processing is very challenging and it can be argued that due to an overload of consent notices, data subjects no longer make active, informed choices but merely agree to such notices when they are asked to do so.Footnote 42 Because users often ‘blindly’ agree to notices that pop up on their screens, the ability to withdraw consent (Article 7(3) GDPR) at any given time becomes (at least in theoryFootnote 43) an important redress mechanism for such situations and extends the control of data subjects beyond the stage of data collection to the entire data lifecycle.
b Data Subjects’ Rights
Next to consent, data subjects’ rights provide individuals with control over the use of their data, which is why they are also referred to as ‘control rights’.Footnote 44 These rights apply notwithstanding whether the processing is based on consent or if another legal basis applies (see Article 6(1)(b-f) GDPR).
Data subjects’ rights include
the right to information (Articles 13 and 14 GDPR), which lists the (comprehensive) information that data controllers must provide to data subjects when collecting their data;
the right access (Article 15 GDPR), which grants data subjects the right to get a copy of the personal data (in a commonly used electronic format) from the data controller and the right to obtain similar information on the processing of their data as provided for under the right to information;
the right to rectification (Article 16 GDPR), which empowers data subjects to rectify inaccurate or complete incomplete personal data;
the right to erasure (Article 17 GDPR), which allows data subjects to have their data erased by the data controller in specific circumstances, namely if the data subject withdrew consent or if the data is no longer necessary for the purposes it was collected for;
the right to restriction of processing (Article 18 GDPR) in specific circumstances, namely if the accuracy of the data is contested or if the data subject has objected to the processing;
the right to data portability (Article 20 GDPR), which enables data subjects to receive their data in a machine-readable format or to transmit it to any third party;
the right to object (Article 21 GDPR) to data processing which is based on public or legitimate (private) interests on grounds relating to their particular situation;
and the right not to be subject to automated decision-making (including profiling) when such an automated decision produces legal effects or similarly significantly affects a data subject (Article 22 GDPR).
Boundaries to these data subjects’ rights are set within the GDPR, either within the data subjects’ rights themselves or through Article 11 GDPR. The latter limits the rights of the data subject when the data controller is unable to reidentify a data subject within its datasets. While the rights to access, rectification, erasure, restriction, and portability do not apply in such cases, the data subjects’ right to information, to objection, and to not being subject of automated decision-making still prevail (Article 11(2) GDPR).
3 Analysis
When personal data is being processed, the GDPR provides a some control to data subjects: Consent is one of the two most important lawful bases of processing, thereby handing the decision whether personal data is processed to the data subject. In addition, data subjects have a well-developed set of rights that allow them to be informed about, to exert some control and quite often also to inhibit the processing of their data by the data controller.
However, the GDPR only provides an amount of control. Most importantly, the lawfulness of the processing can be (and often is) based on the legitimate interests of the controller or public interests; in these instances, the processing of personal data is warranted without the consent and even against the will of the data subject.Footnote 45 Besides, control is also limited, as many of the data subjects’ rights come with essential restrictions. For instance, the right to erasure is only granted if one out of a limited set of situations is given, namely if personal data is no longer necessary in relation to the purpose for which it was collected (Article 17(1)(a) GDPR), if the data subject withdraws consent and there is no other legal grounds for the processing (Article 17(1)(b) GDPR), or if the data has been unlawfully processed (Article 17(1)(d) GDPR). Another example is the right to data portability, which is limited if the personal data is necessary for the performance of a task carried out in the public interest or in the exercise of official authority vested in the controller (Article 20(3) GDPR).
By providing a limited amount of control to data subjects, the GDPR aims to strike a balance between facilitating the free flow of personal data and ensuring that data subjects can exercise control with respect to the processing of their data (Recital 7 GDPR). Thereby, the law balances conflicting interests of data subjects and data controllers and aligns them with the ideal of an adequate free flow of personal data. The ideal of a ‘free flow’ is achieved by establishing a (mostly) harmonized data protection law framework within the EU, while the adequacy of the free flow is guaranteed by enshrining the notion of ownership as (adequately limited) control over personal data.
Compared with the property rights model, ownership as control takes a more balanced approach. In particular, data access rights are seen as a way forward to enable a more (adequate) free flow of personal data within the EU.Footnote 46
D Data Access Rights
I Access by Individuals
1 Access to Personal Data
Data subjects have a legitimate interest in having access to personal data others process about them. Therefore, the GDPR provides data subjects with a right to receive information about the purposes of the processing, the categories of personal data being processed, as well as – if determinable – the period for which the data will be stored (Article 15(1) GDPR). Amongst others, such access empowers individuals to verify the lawfulness of the processing of their personal data (Recital 63 GDPR). More important – from the perspective of the free flow of data – is the right of data subjects to receive a copy of their data from the data controller; if such request is made by electronic means, the controller shall provide the data in a commonly used electronic form (Article 15(3) GDPR). Where possible, the controller should even grant data subjects remote access to a secure system, which provides them with direct access to their personal data (Recital 63 GDPR). The right to obtain a copy is only restricted if such right adversely affects the rights and freedoms of others (Article 15(4) GDPR), namely if providing a copy of the data would harm trade secrets or intellectual property rights (Recital 63 GDPR). At least theoretically, data subjects are thus able to collect and later use all the data that others have about them.
The explicit and fully fledged right to obtain a copy of the personal data is closely linked to the right to data portability,Footnote 47 which the GDPR grants on top of the right of access if the processing is carried out by automated means (Article 20 GDPR). The latter allows data subjects to (re)claim the personal data they provided to the controller in a structured, commonly used and machine-readable format (Article 20(1) GDPR). Data subjects may themselves receive their personal data, transfer it, or have it, directly transmitted to another controller, if technically feasible. However, the scope of the right to data portability is restricted to data ‘provided’ by the data subject and to the instances of processing based on consent or a contract.Footnote 48 As a consequence, all data inferred from the personal data or information predicted by data controllers, will not be subject to this right.Footnote 49 However, the right of access, which is not restricted to data provided by the data subject, may empower data subjects with a right to get a copy of this data all the same.
2 Access to Non-personal Data
Individuals might also have legitimate interests in having access to non-personal data (e.g. text documents, spreadsheets, presentations, or other files that do not contain personal information) that they stored with a service provider, such as a cloud storage or a webmail provider. Such data will most often be processed on a contractual basis. These contracts grant users access to the service providers’ servers to upload and access their files. The applicable terms of service of cloud service providers usually state that the users own the files and that they have a right to access their files, while cloud providers most often reserve the right to access, store, and scan these files (see for instance the terms of service of Dropbox or Google Drive). If the terms of service do not explicitly provide for a user's right of access, courts might derive such right from the underlying contract given that granting access to one’s data is the very nature of such contracts. Accordingly, users should have a right to access non-personal data they provided to a service provider in most cases.
If non-personal data has been stolen, e.g., by hacking a user's device, criminal sanctions apply. In addition to these sanctions, tort law may give users a right to reclaim their non-personal data from the ones that stole it from them.Footnote 50 Even if such claims may be difficult to enforce in practice, the legal basis for access is given.
3 Analysis
Although the law does not provide for a general right of access to all sorts of data, individuals seem to be able to get access to ‘their’ data in most instances where access can reasonably be required. At the same time, data controllers and processors may only process their personal data in accordance with the requirements of the GDPR. Accordingly, from the perspective of the individuals, an adequate free flow of their data seems to be granted (at least in theory).
This is especially true when personal data is being processed as data subjects can draw upon the various control rights established in the GDPR, as discussed earlier. Next to the right of access, the right to data portability is seen as a powerful means to strengthen individual control.Footnote 51 In theory, this right should ensure that data subjects ‘play an active role in the data ecosystem’Footnote 52 and enable them to break up service lock-ins in the digital economy (especially in social media). In this sense, data portability is seen as a means to foster competition,Footnote 53 while simultaneously ensuring an adequate free flow of personal data. However, it is more than doubtful that these goals can be achieved, since the vast majority of data subjects have so far only reluctantly made use of their individual rights.Footnote 54 Also, the mere right to data portability will hardly suffice to overcome the strong network effects which exist in some sectors, especially in social media platforms.Footnote 55 Nevertheless, the right of access and the right to data portability may prove useful for switching providers in other sectors, such as email or cloud storage providers.
When non-personal data that belongs to a particular individual is being processed, data can most often be accessed based on contractual norms and sometimes based on tort law. While these access rights are much less comprehensive than the access rights for personal data, the latter may promote access to non-personal data for two reasons. First, because service providers have to build their systems in a way that allows them to extract the personal data of their users to comply with the right of access granted in data protection law, they need to build their systems in a way that enables them to identify and distinguish personal from non-personal data. Within this process non-personal data that belongs to an individual, such as text documents, can be identified and extracted as well. Second, it is often hard (or even impossible) to distinguish personal and non-personal data, and both types of data are often present in a single file, e.g. in a document that contains information about its author or in an email that always contains information about recipient and sender (at least in the metadata). Accordingly, it might be easier for service providers to provide all the data that belongs to an individual (whether personal or non-personal) if the said individual requests access to their personal data. It, therefore, seems that the current legal situation should also ensure an adequate free flow of non-personal data that belongs to an individual.
II Access by Businesses
1 Preliminary Remarks
Until today there are no general data access rights for businesses, neither with regard to data held by other businesses nor for data held by government agencies. But, of course, businesses can grant each other access to data on the basis of a contract. The default for businesses, however, seems to be that data is regarded as an asset that should not be shared with others. The general approach of collecting and analysing data in-house and via sub-contractors, and ensuring that this data stays within organizations and is not traded with other businesses,Footnote 56 is an essential impediment to the free flow of data and harms the overall digital economy.
As a public good, data could be used by an unlimited number of businesses simultaneously and the use by one business would not interfere with the use of others. Accordingly, granting access rights to businesses would be a meaningful way to enable broader use of data, unravel its potential, and foster competition. While this applies to all sorts of businesses, it is especially true for start-ups and small- and medium-sized enterprises (SMEs), which could benefit from the access to data for developing innovative digital goods and services.Footnote 57 It is therefore not surprising that both the European CommissionFootnote 58 and the OECDFootnote 59 are promoting the digital economy via access rights.
Even if no harmonized legal framework granting access rights for businesses exists, some sector-specific regulations can remedy specific problems. Besides, competition law contains generally applicable rules that may allow businesses to request access to data in some situations. More recently, the introduction of compulsory licences has been promoted in the literature as a new and promising way to establish access rights for businesses.
2 Implementation
a Sector-Specific Regulations
There are three types of sector-specific regulations granting access rights to data: (i) regulations granting government agencies access to data held by businesses; (ii) regulations that provide businesses access to data held by government agencies; and (iii) regulations providing businesses access to data held by other businesses. The first type of access rights ensures that government agencies have access to the data they need to perform their tasks and to take well-informed decisions.Footnote 60 Such access rights are common in many EU member statesFootnote 61 but they are not the subject of this chapter, the enquiry of which is limited to access rights of businesses. The second type of access rights is a means to make better use of the data collected by government agencies by enhancing the reuse of such data. The third type mainly aims at fostering competition.
The most prominent example of the second type of access rights is the EU’s Public Sector Information Directive.Footnote 62 According to this directive, this data must be freely available for reuse and public sector bodies are not allowed to charge more than marginal cost for such reuse.Footnote 63 However, one could argue that if private businesses profit from data provided by the government, the general public should in return obtain some benefits from the data that businesses generate through the use of government data, or that at least government agencies obtain access to such data at marginal costs.Footnote 64
The third type of access rights is not very widespread, at least until today. A case in point is the maintenance work on cars which often depends on access to data about the car. This case is governed by Regulation 715/2007 of the EU.Footnote 65 In order to foster competition in the market for car maintenance, manufacturers of cars must provide unrestricted and standardized access to specified information to repair workshops through websites using a standardized format in a readily accessible and prompt manner (Article 6 Regulation 715/2007). For doing so, the manufacturers can charge a ‘reasonable and proportionate fee’ (Article 7 Regulation 715/2007). Another example is the EU Directive 2015/2366 on payment services in the internal market,Footnote 66 which enables payment service providers to get access to data held by banks in order to facilitate their market access.Footnote 67
b Competition Law
In addition to sector-specific regulations, competition law contains generally applicable rules that may arguably serve as access right. In practice, however, competition law is not a workable solution, for several reasons:Footnote 68 First, with regard to access rights, competition law only comes into play in respect of businesses with a dominant position; even if this condition is met, access can only be requested in case of an abuse of such dominance (Article 102 TFEU). Second, the traditional criteria for defining the relevant market are not very helpful for defining markets in the data economy.Footnote 69 Third, and most importantly, competition law cases take a very long time to be decided, sometimes up to ten years.Footnote 70 It is obvious that businesses requesting access to data need much faster procedures to enforce their rights. Therefore, competition law is not a meaningful way for granting access to data.
c Compulsory Licences
A promising way forward for ensuring access to data is the granting of compulsory licences as known in intellectual property law. As opposed to competition law, where courts define the conditions of granting a licence ex post, the conditions of such compulsory licences are defined ex ante. The difficulty here rests in establishing a system that considers the interests of all businesses involved, the one requesting and the one granting access, especially the latter’s interest in securing its trade secrets.Footnote 71
A general right of access to data would have to be regulated in a generally applicable body of law. A suitable and convincing approach is introducing such a right in trade secrets law. This previously quite heterogeneous body of law has recently been harmonised by the EU’s Trade Secrets Directive.Footnote 72 The directive contains an expansive notion of trade secrets embracing all secret information (i.e. information not generally known or readily accessible) that has commercial value because it is secret and is subject to reasonable steps to keep it secret.Footnote 73 This definition encompasses most data held by businesses. Accordingly, amending trade secrets law would be a promising way to introduce general compulsory licences for granting access to data. While such an approach would be rather broad, compulsory licences could also be granted in sector-specific regulations, such as in telecommunications or energy acts, or in a potential regulation of platforms, covering search engines or social media providers. In any case, access rights should not be granted for free. Rather, any business making use of its right of access should pay a fair, reasonable, and non-discriminatory (FRAND) compensation to the business that has collected, stored, and curated the data.Footnote 74
Even if compulsory licences are considered a meaningful way of granting access to data, many things are still unclear. For example, one would have to define the conditions for granting such a licence and its scope (i.e., the data which is covered), as well as the purpose for which the data may be used if access is granted.Footnote 75 Today’s case law contains some hints to address these important questions – the need for having access to data for entering a secondary market.Footnote 76 Other conditions could relate to single source data situations or some degree of market power of the business that should grant access. Also, one would have to decide whether a compulsory licence includes the right to get a copy of the data or whether such right should be limited to using and analysing the data on the machines of the trade secret owner. Lastly, and most importantly, even if compulsory licences are considered a suitable mechanism for granting access rights, it remains unclear if granting such licences is justified.
The most important argument in favour of introducing compulsory licences is undoubtedly the fact that data is a public good, as discussed earlier. Also, the business of most companies is not selling data to their customers but providing services that are based on data. As a consequence, granting access to data does not necessarily have a negative impact on the market share of the business that has to provide access. If this should be the case, one could consider restricting access to businesses that are not direct competitors but active in a secondary or even in an entirely different market.
The most important argument against granting access rights is the risk of undermining incentives for collecting, storing, and curating data. However, for the time being, it is hard to imagine that well-defined access rights would actually undermine such incentives to a relevant degree.
3 Analysis
Access rights for businesses are a meaningful way to enhance the free flow of data in the digital single market in order to foster innovation and strengthen the competing power of European companies. While competition law is not a workable solution, two complementary approaches seem quite promising: First, trade secrets law could be amended to include compulsory licences, which allow businesses to claim access to data held by other businesses. Given the very broad scope of application of trade secrets law, this approach would allow to establish a general right of access to data. In order to protect the interests of businesses that have to grant access, relatively strict conditions would have to be designed and businesses requesting access would have to pay an appropriate licence fee. Second, sector-specific regulations could grant specific access rights. In such regulations, the conditions for claiming access could be modified and be either stricter or more lenient than in trade secrets law and certainly more specific, also with regard to the calculation of the licence fee. In addition, there might be situations in which access should be granted for free or only if the businesses involved grant each other access on a mutual basis (cross-licence). The combination of these two approaches would allow for a comprehensive regime of access rights, ensure an appropriate balancing of interests, and help establish an adequate free flow of data amongst businesses in the digital single market.
For the free flow to be fully adequate the interests of the individuals represented in the data must be taken into account as well. This is ensured by the application of the GDPR, which regulates virtually all processing of personal data by businesses (Article 2(1) GDPR), including the granting of access to such data. Access to personal data can thus only be granted in accordance with the requirements of the GDPR, namely the principles of transparency and purpose limitation (Article 5(1)(a) and (b) GDPR), the conditions for the lawfulness of processing, namely consent of the data subjects or legitimate interest of the data controller (Article 6(1)(a) and (f) GDPR), the information duties (Articles 13(1)(e) and 14 GDPR), and (if applicable) the conditions for the transfer of personal data to third countries (Articles 44 et seqq. GDPR).
If these requirements are met, one can certainly say that granting access to data through compulsory licences is a promising way to establish an adequate free flow of data in the digital single market. Given that many questions still need to be answered, it is also an avenue that deserves further research.
E Conclusion
In order to unlock the potential of the digital economy, the EU promotes its Digital Single Market Strategy. A core aspect of this strategy is establishing an adequate free flow of data within the Union. This adequate free flow balances economic interests of businesses of an entirely free flow of all types of data and individual interests to have some control of the collection and processing of personal data. To achieve this balance, different regulations have been set in place, such as the Trade Secrets Directive, the Open Data, some sector-specific regulations granting access rights, and, above all, the GDPR.
These regulatory attempts have been accompanied by a policy discussion on data ownership and data access rights. As shown in this contribution, data ownership can be understood both as a form of property and as a form of control. Both concepts are not equally fit to achieve the goal of establishing an adequate free flow of data within the digital single market. The introduction of data ownership as a property right for personal and non-personal data would increase transaction costs and impede the trading and the use of data. Such a right would thus hinder the EU’s goal of achieving a free flow of data. Additionally, in terms of processing personal data, ownership as a property right does not aid individuals to remain in control of their personal data. To the contrary, such ownership rights would substantially weaken their position, as businesses could acquire these rights and exclude the data subjects from using their own personal data. Therefore, the concept of ownership as a property right can be dismissed as a model to help achieve the goals of the Digital Single Market Strategy. The concept of ownership as control has been implemented in the GDPR for the processing of personal data and has the potential to balance economic and individual interests. From an economic perspective, the harmonization of rules and the prohibition of data localization restrictions enhance the free flow of personal data. In contrast, the necessity to comply with the data protection principles (Article 5 GDPR), the need to establish a basis for the lawfulness of all processing of personal data (Article 6 GDPR) and the increased compliance duties of data controllers limit the processing activities and require the establishment of costly organizational and technical solutions to enable data subjects to make use of their individual rights (e.g., right of access and erasure). From an individual perspective, however, these limitations and in particular the (limited) control over how data about them is collected, as well as the options to interfere with the processing of said data at a later stage, are welcomed by many. It remains to be seen, however, whether individuals will actually exercise their (limited) control and whether the current approach of data protection law is able to strike an appropriate balance between economic and individual interests. While some doubts remain, the GDPR can be seen as a first step towards establishing an adequate free flow of personal data within the digital single market.
To achieve the goal of an adequate free flow of data within the EU, individuals and businesses should have access to the data necessary to pursue their interests. For individuals, access to their personal data is key to ensure informational self-determination. Such access is granted by the GDPR, in particular through the right of access and the right to data portability. In most cases, individuals also tend to have sufficient means to access non-personal data that belongs to them. Businesses should have access and be able to use personal and non-personal data as seamlessly as possible in order to develop innovative goods and services and strengthen their competing power, both within the EU and on a global level. The goal of a fully free flow of data, however, must be balanced against the interest of individuals in the protection of their personal data and the interest of businesses in the protection of their trade secrets. Accordingly, a business’ access to personal data held by another business must only be granted in accordance with the GDPR. If these requirements are met or do not apply (as in the case of non-personal data), access to and use of data should be fostered. One way forward is the introduction of additional sector-specific access rights. Another, more all-encompassing and possibly more promising way, is to establish a general right of access to data which is protected as a trade secret by introducing compulsory licences in trade secrets law. Obviously, such licences would only be granted if certain conditions are met, and if an appropriate licence fee is paid. But the mere existence of such licences and the enforcement on a case-by-case basis could help to open up datasets which have been sealed behind corporate walls despite the fact that the data could be useful for others. Overall, the introduction of compulsory licences to grant access to data would allow for the balancing of interests of the businesses holding data with the interests of other businesses that need access to such data to enter a market, develop innovative goods or services, or remain competitive.
A Introduction
The founders of Stitch Fix and Strava understood something basic about people. Humans like to use data to connect with other people and to compare with their peers. Based on those insights, these entrepreneurs were able to build two new digital service companies. Both Stitch Fix (a clothing service) and Strava (a social network) rely on personal data to provide services to their customers. Stitch Fix clients first answer a detailed questionnaire about their clothing likes and dislikes. In return, these customers receive clothes and style recommendations designed by stylists and artificial intelligence (AI) to help them look and feel better about themselves.Footnote 1 Meanwhile, runners, cyclists and triathletes turn to Strava to measure their performance and instantly compare it to others around the world.Footnote 2 The two companies could not succeed without the relatively free flow of data across borders. Data flows move across borders when individuals, companies or governments authorize data to be transferred from one country (the source of data) to another country where the data may be processed or used.Footnote 3
Firms have long relied on data to improve the efficiency and quality of goods and services. However, today market actors also utilize data to create entirely new services, such as personalized healthcare, and sectors such as apps, Internet-connected devices (Internet of Things, IoT), cloud service providers and AI. These sectors are the foundation of the data-driven economy: an economy built around the collection, preservation, protection, implementation and understanding of many different types of data. Although no one has exact figures, a significant portion of the data-driven economy is built on personal data – that is, data by and about people or a person.Footnote 4
The data-driven economy portends major changes for the ability of individuals to shape their destiny and autonomy. Firms active in the data-driven economy are dependent upon data, much of which is personal data. According to the US National Institute of Standards (NIST), in the past, personal data was something that researchers had to ask for, store, analyze. Because it was not easy to collect personal data, scholars struggled to get sufficient information to do a full analysis. But today almost all our daily activities are data-collection opportunities, thanks to the mobile Internet, the IoT, and other data-driven technologies. Moreover, in the past, people could control their data to some extent because researchers, whether firms or individuals, had to obtain, or at least go through the motions of obtaining, consent. However, with the data-driven economy, people whose data is collected and used have provided their personal data without fully informed consent. To put it differently, despite mechanisms to opt in or out of data collection, people do not understand that in return for providing data that firms then monetize, they receive the many free services presented by digital technologies.Footnote 5 In this sense, while the mission of data-driven firms, such as Stitch Fix and Strava may be to help customers, their strategy for so doing may also conflict with long-accepted ideas about autonomy.Footnote 6
Compared to Alibaba or Google, Stitch Fix and Strava are small players in the data-driven economy, but they are not atypical. Many of these firms see providing data services as akin to providing a public good. For example, Google’s corporate mission is ‘to organize the world’s information and make it universally accessible and useful’.Footnote 7 Not surprisingly, researchers and policymakers now believe that data is the most traded good or service. In 2016, the McKinsey Global Institute asserted that the value of data flows has overtaken the value of global trade in physical goods.Footnote 8 According to the World Economic Forum, ‘the world produces 2.5 quintillion bytes a day, and 90 per cent of all data has been produced in just the last two years’.Footnote 9
To succeed in the data-driven economy, companies and researchers need access to significant amounts of data – what economists term ‘economies of scale’. Policymakers in many countries want to encourage these scale economies with shared norms and rules, but they also want these norms and rules to explicitly limit trade in some types of data to ensure the safety and privacy of their citizens. In elaborating this rule framework decision-makers must develop a process that reassures their citizens that the rules-based system is transparent, accountable and open to citizens’ input.Footnote 10 With shared norms and rules, the Internet would be less likely to fragment; more people would have greater access to information; and individuals could create and share more information.Footnote 11 Individuals might also be better able to obtain rents from their personal data and have some modicum of control over its use. However, policymakers around the world disagree on how and where to develop such shared rules.Footnote 12
Many executives and policymakers argue that trade agreements are the appropriate venue in which to govern cross-border data flows, because they believe that when information flows across borders, these flows are essentially traded.Footnote 13 They have negotiated e-commerce and digital trade chapters for this purpose. Herein, we distinguish between e-commerce (goods and services delivered via the Internet and associated with a transaction) and ‘digital trade’, which includes ‘e-commerce’ as well as new data-based services, such as Stitch Fix, or social platforms, such as Twitter.Footnote 14
While countries have begun to build a regulatory environment for e-commerce, it is unclear how to build an effective enabling environment for data. Many developing countries are not yet ready for such rule-making. After all, the bulk of firms like Strava and Stitch Fix are being created in middle-income and wealthy countries.Footnote 15 In many developing countries, business people are hobbled by obstacles such as unstable Internet connections, limited funding, inadequate numbers of researchers, and complementary policies, and infrastructure.Footnote 16 Moreover, while many countries have open data strategies for government-funded or public data, others have not yet figured out how to ensure that when firms mine the personal data of their users, they protect it from misuse, theft, or human rights violations. Firms that do not adequately protect the data that they collect, monetize, and share could lead users to experience problems such as identity theft, manipulative marketing or discrimination.Footnote 17 Users deserve a chance to shape new rules and to influence how firms use data.Footnote 18
This chapter examines the new role of data in trade and explores how trade in data differs from trade in goods and services. Clearly, data is different and may need a distinct set of rules. Although there are six different types of data, we focus on two types: public data and personal data (information that relates to an identified or identifiable individual). We then examine several analogies used by analysts to describe data as an input, which can help us understand how data could be regulated. Next, we discuss how trade policymakers are regulating trade in data and how these efforts have created a regulatory patchwork. Finally, we suggest an alternative approach noting that any agreement must be built by and for the people whose data serve as its foundation. Before trade negotiators try to develop rules regarding cross-border data flows, they must acknowledge the special character of data and focus first on creating an effective enabling environment, then built trust in that new economy by empowering people around the world to control their data.
B The Peculiarities of Data and the Role of Data in Trade
Data and information have long been a key component of trade, but as noted earlier, data has also created new forms of trade. However, cross-border data flows are quite different from trade in goods or other types of services for many reasons: First, many services from payroll to data analytics rely on access to cross-border data flows. These data flows may yield a good or a service, or both.Footnote 19 Second, trade in digital services differs from trade in other services because suppliers and consumers do not need to be in the same physical location for a transaction to occur. Third, trade in data is fluid and frequent, and location is hard to determine on the borderless network. Trade in the same set of data can occur repeatedly in nanoseconds – for instance, when millions of people download Drake’s latest song. As a result, researchers and policymakers may find it hard to determine what is an import or export. They may also struggle to ascertain when data or data sets are subject to domestic law (such as intellectual property law) and what type of trans-border enforcement is appropriate.Footnote 20 Fourth, when data flows across borders, it may or may not be affiliated with a transaction. Hence, it is hard to describe some of these flows as ‘traded’.Footnote 21 Fifth, economists generally agree that many types of data are public goods, which governments should provide and regulate effectively. Furthermore, when states restrict the free flow of data, they reduce access to information, which in turn can diminish economic growth, productivity and innovation domestically and globally.Footnote 22 Such restrictions can also affect the functioning of the Internet.Footnote 23 Sixth, trade in data occurs on a shared platform (the Internet) that is held in common. Seventh, and as earlier mentioned, much of the data flowing across borders and powering new sectors is personal data – digital data created by and about people. While they may benefit from services built on that data, the people who are the source of it do not control it. Data is their asset, yet they cannot manage, exchange and account for it.Footnote 24
Recent surveys show that people around the world are increasingly concerned about how firms use, protect, control and trade personal data. A 2018 poll of 25,262 Internet users in twenty-five countries found that half of Internet users surveyed are more concerned about their online privacy than they were a year ago, reflecting growing concern around the world about online privacy and the power of social media platforms.Footnote 25 Citizens want their governments to strengthen data protection laws and to beef up enforcement. In 2017, the Australian government stated that ‘governments that ignore potential gains through consumer data rights will make the task of garnering social license needed for other data reforms more difficult’.Footnote 26
In sum, cross-border data flows may not fit the traditional definition of trade. Policymakers should thus at least question whether the traditional model of trade rules needs reforms to reflect the specificities of data.
C New Uses for Data Require New Ways of Thinking about Data
When individuals try to describe how firms are using data to reorder markets, they often compare data to other longstanding inputs to the provision of goods and services. In so doing, they hope to create greater understanding of the import and value of data. As an example, the World Economic Forum describes data as the oxygen of digital life.Footnote 27 In contrast, The Economist describes data as a new type of raw material, such as oil, on par with capital and labour.Footnote 28 However, law professor Lauren Scholz notes that this analogy is not helpful because the supply of oil is limited and only one actor can use a given portion of oil at one time. However, if you have access to data, then you can use it to create information and value.Footnote 29 Other analysts describe data as a form of capital, which can be shared and leveraged within and between organizations.Footnote 30 They note that the big data firms, such as Google, Facebook, Amazon, Uber, Stitch Fix and Strava, commodify and monetize data, creating new revenues and/or functions for the company.Footnote 31
Meanwhile, some other scholars posit that we should think about data as labour, as in the early phases of the industrial revolution. We provide our data for free to firms that turn around and monetize this information. But you and I, like the workers of yore, lack bargaining power and are unable to meaningfully negotiate over payments for our data. Most of us are not sufficiently protected from misuse of our personal data or violations of our privacy. In this way, we are denied a share of the economic value of our data, just as workers in the early industrial age. We are facilitating a massive transfer of wealth from ordinary people to the tech titans.Footnote 32 In search of evidence, two scholars traced the AI supply chain and found invisible labour, outsourced or crowdsourced, hidden behind interfaces and camouflaged within algorithmic processes. They note ‘[s]ometimes this labor is entirely unpaid, as in the case of the Google’s reCAPTCHA. In a paradox that many of us have experienced, to prove that you are not an artificial agent, you are forced to train Google’s image recognition AI system for free, by selecting multiple boxes that contain street numbers, or cars, or houses’.Footnote 33 Moreover, these scholars note that treating data like capital exacerbates inequality and limits the productivity gains from big data and AI. They suggest that we should organize collectively to form a ‘data labor union’ that would bargain for fees for assessing our data. The union could certify data quality and guide ‘users to develop their earning potential’. Meanwhile, data collectors ‘must allow users to understand, withdraw, and transfer their data across competitors’.Footnote 34 Only by organizing collectively can we control how our data are used.
Still other scholars argue that personal data is a form of property that individuals can assert rights to control and to access.Footnote 35 This concept underpins the European Union’s General Data Protection Regulation (GDPR). The notion that data is a form of personal property that people should be able to control also undergirds other countries’ approaches, such as those of Brazil and China.Footnote 36
If we view data as property, then corporations would have to pay the data generators (you and I) for permission, collection and use of data. The big firms would probably not offer services for free if we had to pay. Moreover, firms would then have an incentive to keep data accurate and carefully stored.Footnote 37 But law professor Lisa Austin warns that if you think about data as property, you have to balance the ownership claims of the owners of personal data with those of the firms processing and monitoring that data.Footnote 38 Nor can we ensure that our private information is not misused. As law professor Teresa Scassa has noted, privacy laws are ill fitted to a context in which data is a key economic asset.Footnote 39
Finally, the UK government has introduced the notion that data is similar to infrastructure. In a paper prepared for the National Infrastructure Commission, the authors noted ‘the managed and built environments increasingly depend upon data in real time. New mechanisms for the assembly, management and processing of data provide a new impetus for thinking how the data is best managed so that society can best utilize its resources, solve the most problems and provide the most social good for most people’.Footnote 40 In this view, government plays an important role providing and regulating data and promoting its sharing and consumption.Footnote 41
Except for data as property, these analogies have not significantly influenced national and international regulations. Moreover, these analogies miss an important aspect of the nature of personal data. It is a by-product of our thinking, actions and simply living. It is not one thing, and thus, we should not simply view it as a resource, or as our property, capital, labour, or infrastructure.
There are no reliable statistics about the types, value and amounts of data exchanged across borders and what percentage of cross-border data flow consists of personal data. Both CanadaFootnote 42 and in the United States,Footnote 43 are trying to estimate the value of these flows. Despite the lack of exact numbers, we can hypothesize that a significant portion of the data exchanged across borders is personal data. People’s ability to control their data, like other issues of autonomy, is becoming a civil rights issue.Footnote 44 According to Ravi Naik, individuals’ rights to data protection ‘have too often been ignored, and it is taking a groundswell of citizen activism to flip the script and hold power to account by individuals asking for their data and determining its use. We are at a watershed moment of a citizen-led demand for data rights, with the hallmarks of a new civil rights movement enmeshed within it’.Footnote 45 Some countries, such as Chile, Colombia, Mexico, Turkey and Ecuador, are making personal data protection a constitutional right, although they differ as to the efficacy of enforcement.Footnote 46
Truth is, these analogies can only go so far in guiding public policy because the new economy is behaving in ways that few of us understand. For example, the market for data is opaque: we really do not know how firms use our data. In these conditions, data holders/gatherers can deny or grant access to data; they do not have to let people know what data they have collected, whether it is accurate, how they use it and if they sell it.Footnote 47 In opaque markets, policymakers should develop policies that facilitate transparency and accountability, as counterweights to opacity. Breznitz argues in this sense that governments must establish the market for data and set the rules for how data are gathered and used.Footnote 48 Meanwhile, the Australian Productivity Commission says that governments must move markets from a system based on risk aversion and avoidance (which is not working) to one based on transparency and confidence in data processes.Footnote 49
Despite their flaws, two of these analogies may be useful to trade policymakers, as they seek to develop rules governing cross-border exchange of data. First, at the national level, developing country policymakers who see data as a form of basic infrastructure could be more willing to establish data plans. Smart management of all types of data will enable more people to benefit from such data and to create new data-driven services attuned to specific economies and cultures. In contrast, the data as labour analogy might help trade policymakers as they attempt to bridge national strategies and create international rules governing data. In the late nineteenth century, many industrializing states developed national regulations to improve work conditions and protect workers from the vagaries of globalization. These regulations helped raise wages, which in turn led to improvements in labour productivity and greater trade. But not all states adopted such worker protections and trade policymakers feared a race to the bottom among states competing for lower wages and working conditions. The members of the League of Nations established an International Labour Organization (ILO) with rules that would help them find common ground to improve workplace conditions, facilitate peace and encourage trade.Footnote 50 We may need a similar organization to help mitigate the differences among national data approaches, if not the WTO.
D The Current State of Rules Governing Cross-Border Data and the Rise of Data Realms
Policymakers have been trying for years to create global rules to govern cross-border data flows both at the World Trade Organization (WTO) and in bilateral and regional trade agreements. The multilateral trade forum of the WTO includes several agreements that address issues affecting data and digital trade. They include the Information Technology Agreement; the Agreement on Trade-Related Aspects of Intellectual Property Rights (TRIPS); and the General Agreement on Trade in Services (GATS). The GATS is the most relevant to the new data-driven services; it has chapters on financial services, telecommunications, computer and media services. But the GATS predates the invention of the Internet and World Wide Web and says nothing explicitly about cross-border data flows. Nonetheless, the WTO panels and the Appellate Body have interpreted the agreement as applying to various online services. While they acknowledge that the agreement is technically neutral – that it was written to apply to changing technologies – academics, business leaders and various governments, including the United States, have argued that the WTO’s rules need both amplification and clarification to apply to new data-driven services, such as those provided by Stitch Fix and Strava.Footnote 51 Meanwhile, WTO members established a work programme on e-commerce in 1998 and have agreed to waive customs duties on electronic transmissions. They also appear to have made progress on negotiations on data, as a leaked text reveals.Footnote 52
At the Eleventh WTO Ministerial Conference in Buenos Aires in December 2017, Australia, Japan and Singapore, with the support of sixty-seven other WTO members, launched the E-Commerce Joint Statement Initiative. They hoped to encourage a consensus on what members should negotiate and how.Footnote 53 To further that effort, countries issued proposals and background papers. A group of African countries, also supported by India, advocated keeping the discussions within the WTO’s current exploratory work programme, which has conducted work on e-commerce-related topics within various WTO bodies, such as its Council for Trade in Services and Council for Trade in Goods.Footnote 54 Overall, not only is there a lack of consensus on e-commerce issues among the members but also it is often apparent that many of the members do not understand the differences, nor do they clearly distinguish between e-commerce and the provision of data-driven services.Footnote 55
Despite this, on 25 January 2019, some seventy-six WTO members agreed to commence dedicated e-commerce talks. The announcement of this initiative was not greeted with universal acclaim. While business groups lauded it, civil society organizations and international labour groups came out against the talks and argued that a new agreement could threaten jobs, privacy and data security.Footnote 56 The members of the WTO did not only disagree about whether or not these talks should proceed, they also disagreed about the scope of the talks.Footnote 57 Many states – including the United States, Canada, China, Japan, the EU, Australia, Brunei, Hong Kong, Kazakhstan, Korea, Mongolia, New Zealand, Singapore, Chinese Taipei, Thailand, Georgia, Iceland, Liechtenstein, Moldova, Montenegro, Norway, Russia, Switzerland, Macedonia and the Ukraine – are keen to move the talks forward. With regard to data flows in particular, while the United States, Canada, the EU and Brazil generally want to create interoperable and universal rules and limit barriers to cross-border data flows, Russia and China are more concerned with maintaining internal social and political stability and are more open to using domestic regulation to limit such flows.Footnote 58 Developing countries are also divided. Policymakers and business leaders in most countries acknowledge that traditional e-commerce could help their farmers and firms trade directly with consumers around the world.Footnote 59 So, they are willing to negotiate ‘e-commerce’, but many are leery of negotiating data-driven services, given that they may lack domestic data-driven firms.
Meanwhile, the United States, the EU, Australia, Canada and other nations have placed language governing cross-border data flows in e-commerce chapters of their free trade agreements. As the data-driven economy has expanded in importance, the US, Mexico, Canada, the EU and Japan have recently renamed the newer versions of these chapters ‘digital trade’ chapters. Nations are also negotiating and agreed to digital economy specific agreements such as the Digital Economy Agreement of Australia and Singapore, US Japan Digital Economy Agreement, and the Digital Economy Partnership of Chile, New Zealand, and Singapore.Footnote 60
The first agreement, the Comprehensive and Progressive Trans-Pacific Partnership (CPTPP) went into effect in 2019 among eleven nations bordering the Pacific including Australia, Japan, Mexico, Chile and Canada. These nations agreed to the free flow of data across borders as a default, with limited exceptions. All signatories also must adopt a minimum level of privacy regulation. In contrast, the EU–Japan Free Trade Agreement (FTA), which also went into effect in 2019, puts personal data protection at its core. The EU–Japan Free Trade Agreement is the first FTA of the EU that includes rules on data but it also ensures that personal data is adequately protected not only under the agreement but additionally through an adequacy decision of the European Commission – the first such decision under the GDPR heightened standards of data protection.Footnote 61
The US government next used CPTPP, whose e-commerce chapter is identical to that negotiated under the Transpacific Partnership Agreement (TPP) as a building block for the renegotiation of the North American Free Trade Agreement (NAFTA). NAFTA 2.0, now called the United States–Mexico–Canada Agreement (USMCA), has several interesting elements designed to promote data-driven economic growth. It seems designed to promote AI and other data-driven services. First, the USMCA contains a proper chapter on ‘digital trade’ (chapter 19), rather than one on e-commerce. Secondly, like CPTPP, it bans mandated disclosure of source code. But differently from the CPTPP, it also promotes AI by encouraging the parties to provide public information (information developed or provided to public entities) in a machine-readable and open format that can be ‘searched retrieved, used, reused, and redistributed’.Footnote 62
While the United States and Canada have made regulating barriers to cross-border data flows a priority, the EU has made personal data protection a priority. The EU will only sign FTAs that contain language regarding the free flow of data if its FTA partner(s) adequately protect personal data. These nations must go through a process of becoming ‘adequate’. Specifically, these states must create independent government data protection agencies, register databases with those agencies and, in some instances, obtain prior approval from the European Commission before personal data processing may begin.Footnote 63 This process is both time-consuming and expensive, as the EU’s digital trade partners must devote resources to data protection, a difficult choice for nations with limited governance expertise or funds.
Meanwhile, policymakers in China restrict the free flow of data and information not only across borders but also within China. In so doing, Chinese officials maintain social stability and the power of the Communist Party.Footnote 64 However, China participated in the negotiation of Regional Comprehensive Economic Partnership (RCEP), a mega-regional trade agreement. RCEP includes Australia, Indian, Japan, South Korea and New Zealand as well as the nations of the Association of Southeast Asian Nations (ASEAN).Footnote 65 The RCEP' allows member states to impose whatever national regulatory restrictions they wish, as long as they are applied in a non-discriminatory way (are applied equally to domestic and foreign businesses).The provisions are not disputable.Footnote 66
Thus, the three big digital markets – the United States, EU and China – have taken different approaches to cross-border data flows. This patchwork approach is causing another problem for many nations. Nations, such as Canada, Mexico and Australia, that have or seek to build strong trade relationships with the big three must choose which approach they would follow.Footnote 67 Countries that choose more than one such market will face high regulatory costs, as their costs of compliance would rise, given different standards.Footnote 68
In a recent scholarly study, the WTO secretariat confirmed this patchwork of rules. It examined regional trade agreements that have incorporated specific provisions related to e-commerce. They found significant heterogeneity among the seventy-five chapters that explicitly address e-commerce. For example, these FTAs have different objectives, scope and definitions. The FTAs also define and limit different barriers to trade, and most importantly, some thirty-eight of the seventy-five have different provisions related to the domestic legal framework in which e-commerce takes place. Finally, some forty-four of the seventy-five include language on personal data protection but again with very different definitions and obligations.Footnote 69
Developing countries are likely to have the most problems adapting to the data-driven economy. These countries will be customers of AI and other data-driven sectors, rather than producers. According to Kai-Fu Lee, a venture capitalist and former computer scientist, the bulk of profit from the data-driven economy and particularly AI will go to the United States and China: ‘AI is an industry in which strength begets strength: The more data you have, the better your product; the better your product, the more data you can collect; the more data you can collect, the more talent you can attract; the more talent you can attract, the better your product. It’s a virtuous circle, and the USA and China have already amassed the talent, market share and data to set it in motion’.Footnote 70
Finally, many developing countries have not yet adopted effective rules protecting personal data online or established rules for the use of public data. Based on data from 2017 the UNCTAD reports that 57 per cent of all countries (some 107 countries of which 66 were developing or transition economies) have put in place legislation to secure the protection of data and privacy. In this area, Asia and Africa show a similar level of adoption, with less than 40 per cent of countries having a law in place. Some 21 per cent of countries have no law at all; and 10 per cent are in the process of drafting legislation.Footnote 71 Moreover, most of adopted legislation contains rules that are not consistent with either the OECD Guidelines for the Protection of Personal Information and Transborder Data FlowsFootnote 72 or EU’s GDPR.Footnote 73
Moreover, some countries hoard and refuse to share publicly held data with their citizenry.Footnote 74 In general, data gains value as it is shared, but it has little value if governments hoard it. While there is little empirical proof, open data appears to have important spillover effects including increasing civil discourse, improved public welfare and a more efficient use of public resources. But many states lack right to information laws or do not allow their citizens to view or comment on the data they hold.Footnote 75 So not only is there a patchwork for FTAs but there is also a patchwork of approaches to governing various types of data as well.
Without sufficient understanding and interaction with data-driven firms and their customers, developing country policymakers may struggle to effectively advocate for their short- and long-term interests in the data-driven economy. Zimbabwe provides an example: the government signed a strategic cooperation framework agreement with a Chinese start-up, CloudWalk Technology, for a large-scale facial recognition programme. Zimbabwe will export a database of their citizens’ faces to China, allowing CloudWalk to improve their underlying algorithms with more data. The government allegedly agreed to the system to improve public safety, while the company wanted to improve the accuracy of its facial recognition system which was based on Chinese faces and needed a wider range of facial types. However, the government of Zimbabwe could use this system to more closely monitor its citizens, which could undermine social stability and trust.Footnote 76 While such a situation may be rare, it provides a strong rationale for Zimbabwe and other countries to develop and debate a strategy for protecting personal data.
E A Path Forward
Humans have long exchanged data between borders, but never have they traded so much data or benefited from so many new services built on data. These new services may make us smarter, richer, more flexible and more efficient. But not all countries or people are ready to participate in this brave new world. The OECD recently noted that ‘governments and stakeholders have a responsibility to shape a common digital future that improves peoples’ lives and boost economic growth for countries at all levels of development, while ensuring that nobody is left behind’.Footnote 77 However, for governance to succeed and be trusted, it needs to be built on shared norms and rules.
Policymakers should first work at the national level to develop a national strategy for data and then move towards interoperability of approaches rather than harmonization. They must find a way to conduct discussions on data governance that build public trust, consistent with the multi-stakeholder processes embedded in other forms of Internet governance. Against this backdrop, this chapter suggests five steps for moving forward, summarized below.
Step 1: Encourage States to Develop Plans for the Regulation and Exchange of Different Types of Data
Given the complexity of data, its role in new services and the importance of data to economic health and political stability, every nation should develop a strategy for how public and personal data are to be used and exchanged across borders (a national data plan). The plan should focus on ensuring that most public data sets are open, and personal data, especially personally identifiable information,Footnote 78 is adequately protected. Such a plan should address issues of ownership, control, equity (i.e. that the data is developed and analyzed in an even-handed manner) and monetization of data (who can earn money for data and how). Policymakers will also have to address issues related to the cloud and data transfer – how a country can control the transfer of data that might include personally identifiable information or data that is important for national security.Footnote 79
It will not be easy for most states to develop such a plan. Policymakers will need guidelines, incentives and technical assistance. Most advanced economies are in the early stages of developing such plans, as they wrestle with disinformation, ethics of AI and digital disruption of various sectors. But some nations/trade blocs are way ahead. The EU, for instance, has developed an EU-wide data strategy focusing on types of data, giving citizens in the EU some control over use of their data. The EU has also established a road map which enables EU policymakers to monitor member states’ progress.Footnote 80 Meanwhile, the UK, Canada and Australia are in the process of developing their own data plans to match their digital trade strategies. Mexico, Australia and Brazil have too put forward public data or data innovation strategies and Canada is in the process of developing one.Footnote 81 In addition, some countries are putting in place plans to facilitate the development of data-driven sectors. As an example, the seventy-five members of the Open Government Partnership pledge to develop plans to make public data open to all. The D7 is a group of countries (Estonia, Israel, New Zealand, South Korea, the UK, Canada and Uruguay) committed to encouraging the data-driven economy and e-government.Footnote 82
International trade and development organizations, such as the World Bank and UNCTAD, could work with civil society groups skilled in data issues (such as Privacy International or the Open Government Partnership) to bring these issues to the fore and provide technical assistance.
Step 2: Give People Greater Voice and Greater Control over Their Data
For the data-driven economy to succeed it must be built on a foundation of trust, and users must have legal protections and greater control over their data. A growing number of data protection plans include some element of consumer control over personal data. Policymakers should call for an international meeting to establish an interoperable approach to data protection and control, which allows nations to evolve their own complementary approaches. The meeting should be attended by a diverse set of individuals, firms and agencies involved in privacy and data protection issues, and it should be tasked to build on existing principles, such as the APEC and OECD Privacy Principles.Footnote 83 The organizers of such a meeting could establish a website that will be ‘marketed’ by participating governments. The architects of the site could then ask netizens to crowdsource ideas about how to build on these existing principles while simultaneously empowering people to control their personal data.Footnote 84 Companies and data protection officials have already found some common ground on helping companies that move data globally to transcend different regulatory strategies.Footnote 85 But there seems to be a growing sense that the US approach is too focused on ensuring that personal data can be utilized as a commercial asset, while the EU has put its citizens first and protect their personal data as a matter of a fundamental right.
Step 3: Clarify the Rules and Exceptions to the Rules, So Nations Do Not Restrict Cross-Border Data Flows More Frequently or Broadly than Necessary
Like other treaties, a data-driven economy agreement should include exceptions to the rules. Nations can use the exceptions to ‘excuse’ violations to the agreement when they pursue other important policy objectives. (Figure 16.1 shows that governments have a wide range of reasons to restrict cross-border data flows.) Countries can only use these exceptions, however, if they do so in the least trade distorting manner. Yet, so far, there is no clear model that policymakers can follow to distinguish between legitimate and trade-distorting data flow regulation. The current language in trade agreements is vague and states must rely on trade disputes to develop clarity and some degree of legal certainty. However, there have been few disputes to provide guidance and policymakers have not yet agreed on updating the WTO law language with regard to the general exception clauses or other specific exceptions.

Figure 16.1. Why and how do governments restrict cross-border information flows? Prepared by Caitlyn Leong
Policymakers should begin by delineating how and when nations can use the exceptions to limit cross-border flows in the name of protecting domestic security or cybersecurity. For example, some governments, such as India, Brazil, the United States and the UK, have called on companies to provide backdoors to encrypted communications to help law enforcement. However, such an encryption backdoor would undermine trust and the effectiveness of encryption as a tool for keeping individuals, firms and governments safe online.
Step 4: Provide Clarity on What Types of Practices Should Be Banned Because They Are Trade Distorting
Beyond data localization and taxation of e-commerce, there is little agreement as to what measures distort cross-border data flows.Footnote 86 For example, many Western countries believe that censorship is a trade barrier, which can undermine the many benefits of the Internet. Yet, no trade agreement discussing cross-border data flows mentions censorship, filtering or Internet shut-downs as a barrier to trade that should be regulated. Many states censor, filter or shut down the Internet for a variety of reasons, including safeguarding government authority, fighting terrorism, maintaining national security or protecting local businesses. When they censor, filter or shut down the Internet, they determine what data will be available within their borders.Footnote 87 Authoritarian states are not the only states that censor data. The Indian government, the world’s largest democracy and a technology leader, has had fifty-four Internet shut-downs, more than any other nation in 2017. Human rights groups view these shut-downs as an intentional form of censorship which distorts the free flow of data. These shut-downs have also huge economic costs, estimated at some $3 billion for the period 2012–2017 for India alone.Footnote 88 Brookings scholar Darrell West estimated that globally, Internet shut-downs cost some $2.4 billion in 2015 alone.Footnote 89 Policymakers must find common ground on defining and regulating these practices or they cannot reap the benefits of economies of scale on data. Such practices may also create costly spillovers, such as reducing Internet stability and hampering scientific progress.Footnote 90
Step 5: Delineate How Nations Should or Should Not Respond to State Actions That Distort Cross-Border Data Flows
Trade agreements allow signatories to respond to the trade distorting practices of their partners with compensatory practices. The agreement should clearly state that party responses should be limited and proportional in such instance and define accordingly the legal test. Moreover, any agreement should also clearly state that adopting protectionist strategies, such as tariffs and quotas, or turning to strategies, such as malware, are inappropriate responses, which could reduce cross-border data flows, are prohibited. According to trade scholar Patrick Leblond, ‘Ideally, the response should increase the costs of doing business and penalize proscribed practice, but not penalize the sources of data’.Footnote 91 Data protectionism will beget further data protectionism and undermine the utility of the Internet.Footnote 92 We may be seeing evidence of this digital trade wars already between the United States and the EU: After the US Secretary of Commerce Wilbur Ross called the EU approach to data protection trade distorting in May 2018,Footnote 93 the EU proposed tax and regulatory policies to challenge what some see as the monopolistic control of US Internet giants.Footnote 94
F Conclusion
The world is awash with data and there is no consensus on how to regulate it. The five outlined steps can help nations prepare for future negotiations and build value from data. These ideas will not address all the issues that arise in regulating cross-border data flows, and any new approach is likely to face many challenges, especially from those vested in the existing organizations and approaches to governing data. But clearly, we are stuck in a rut on trade and must creatively address the trade and non-trade dimensions of cross-border data flows. Policymakers from a wide range of countries may be more willing to compromise if they see that their citizens will benefit from clear, interoperable rules and from receiving funds for their data. Moreover, this approach could help firms accommodate national differences regarding ethics of data usage, disinformation and other upcoming regulatory issues. It could also give developing countries greater leverage in the discussions on data flows, where they would ordinarily be ‘rule takers’.Footnote 95 Finally, these ideas could help more countries better integrate data-driven firms and their traditional firms. By collaborating and rethinking the process of global rule-making on data, we will be better able to achieve the change we wish to see in the world – where people have greater autonomy and control over their data and data drives equitable growth.